An event from the "PROdemo: Software Solutions Laboratory" series — a special project by the OCS Soft team. During the meeting, Dmitry Shcherbatyuk, pre-sale expert on information security at OCS, spoke about the PT NAD network traffic behavioral analysis system for detecting hidden cyberattacks and the PT Sandbox expert sandbox for protecting against complex malware and zero-day threats.

In the program:
- Description of product capabilities;
- Description of the data theft scenario from the infrastructure;
- Step-by-step description of the attacker's actions.
Dmitry Shchebatyuk: today we will talk about PT NAD and PT Sandbox, also known as Anti-APT.

We will briefly talk about both products, look at their capabilities and tasks to be solved. And in general, we will briefly consider what Anti-APT is.
Any conversation about cybersecurity should start with the threat landscape.
The dynamics of threats are growing from year to year. At the moment, attacks have been recorded in almost all spheres of activity. This includes industry, trade, medical institutions, science, and education. Since 2022, we have been in a state of cyberwar.
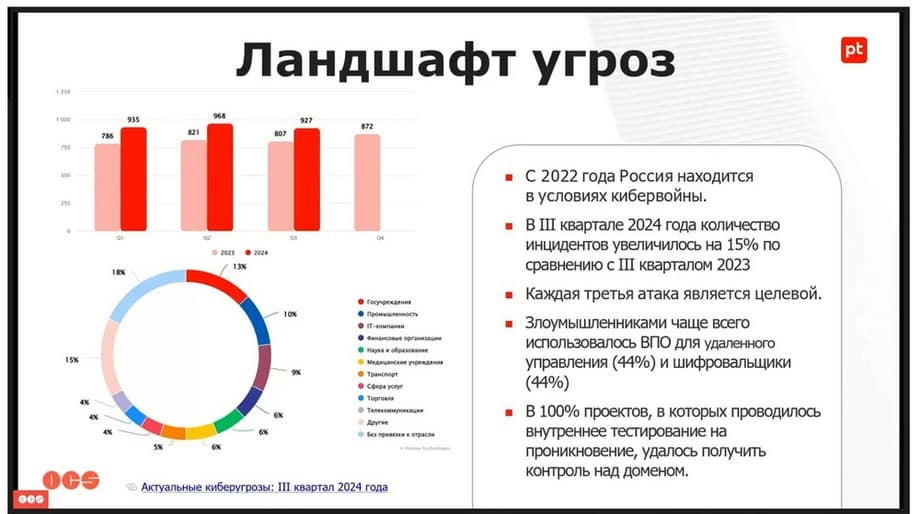
I think everyone has already felt this to some extent. According to the results of the third quarter, compared to the same period last year, the number of cyberattacks has increased by 15%. Now attackers have begun to use not only ransomware, as was the mainstream last year. Software for remote management is also used now. And according to the test results, in 100% of cases, in 100% of projects in which internal penetration testing was carried out, it was possible to gain control of the domain.
How does an attacker get into the network?
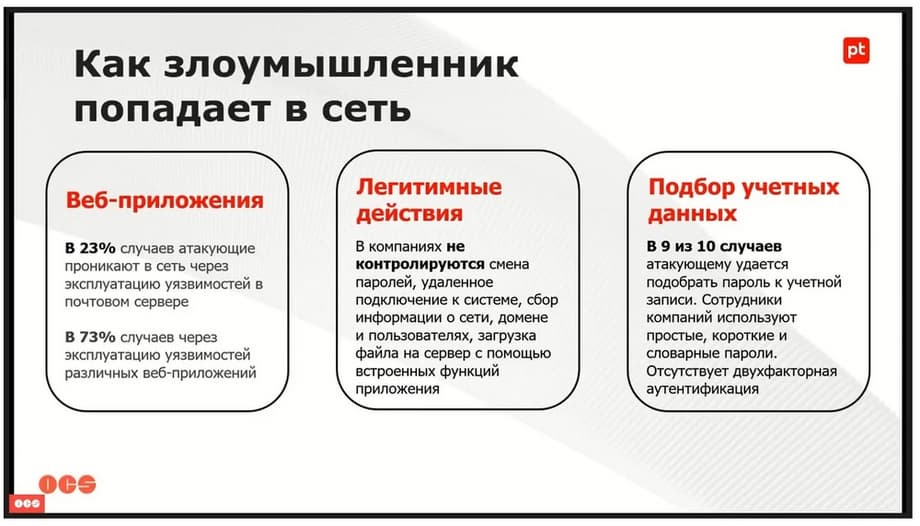
Most often, an attacker penetrates either through the mail server or through a web application. The most common cases of vulnerability occur through web applications, corporate websites, the same Bitrix. For example, phishing is an attempt to penetrate. An email arrives, some manager, very busy, clicks on the email, opens it, and that's it, the attacker has entered the network. Here is a very simple example of how an attacker penetrates through perimeters.
Next, passwords. Attackers no longer just attack en masse, they now mainly study the victim for a very long time, conduct research, study specific people, specific company specialists, and guess passwords. Now, even with our experience of pilots this year, password policies are rarely applied. Such organizations where a strict password policy is applied, I have met only two or three this year. Mostly, employees use simple, often dictionary passwords. When we come to a project with the same PT NAD, we see all these dictionary simple passwords in the open. And all this is easily accessible. And virtual everywhere there is no factor authentication. That is, this is something that should have been introduced a long time ago, but at the moment there is practically none of it.
Moreover, in addition to the password policy, we mainly do not control either remote connections, or the collection of information over the network, or requests to domains from users, or even it is not clear from whom, some file downloads from external systems. All this is mainly not controlled. This is a generalized picture. And this gives attackers a very large field for activity in terms of penetration.
Once an attacker penetrates the network, everything becomes quite bad in reality. In general, if we talk about internal regulations and the internal security structure, we virtual never see a segmented network. And this gives the attacker the opportunity to conduct not just some targeted attack, but he can act immediately in several directions.
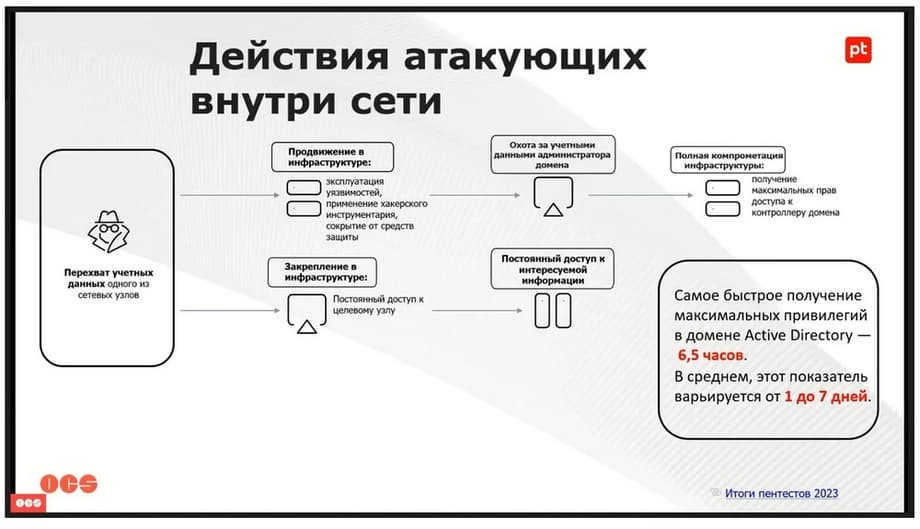
On the one hand, he can simply move through the infrastructure, take administrator credentials there, which are not so difficult to obtain after entering the infrastructure. Again , many people have it simply in open access. Moreover, to exploit certain vulnerabilities, to carry out an unacceptable event, it is not necessary to obtain administrator rights at all. On the other hand, an attacker can simply gain a foothold in the infrastructure and have constant access to the nodes of interest to him , where there is some internal secret information. He can easily receive it.
So, according to recent studies, the fastest way to obtain maximum privileges in the domain is 6.5 hours. Do you understand? 6.5 hours from the moment of penetration to obtaining full control. On average, this figure, of course, varies from 1 to 7 days. But I prefer to rely on the minimum figures when talking about cybersecurity. So, what do we have as a result?
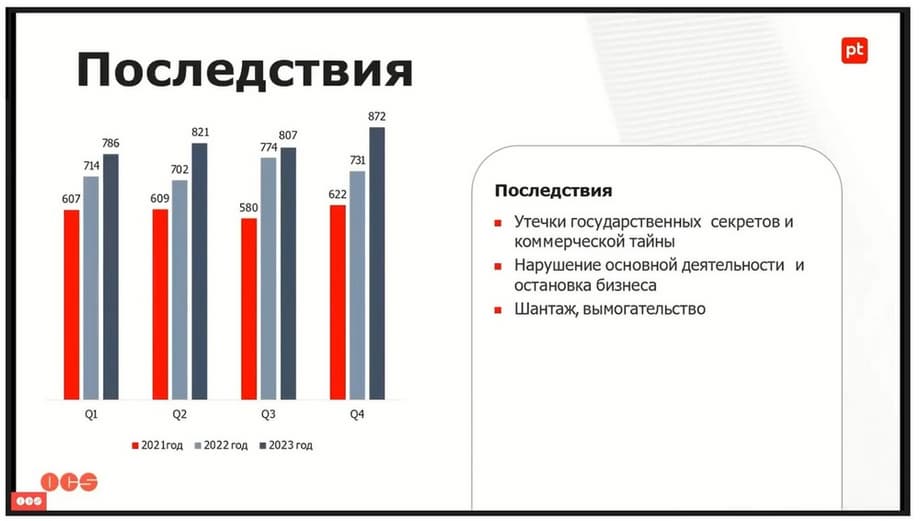
The consequences are usually extremely sad. And these are not only financial losses, although they can be simply catastrophic. (Let's remember SDEK.) This includes disruption of the company's core activities, business stoppage, leakage of trade secrets, state secrets, etc. Attackers sometimes reinforce the fully encrypted infrastructure and then demand large sums for its unblocking. But you will never get a guarantee that by paying this amount, you will actually get the unblocking. The graph shows that the number of incidents is unfortunately growing every year.
The problem is clear. To solve these problems, we offer our products. For network monitoring , we have an NTA class solution PT Network Attack Discovery.
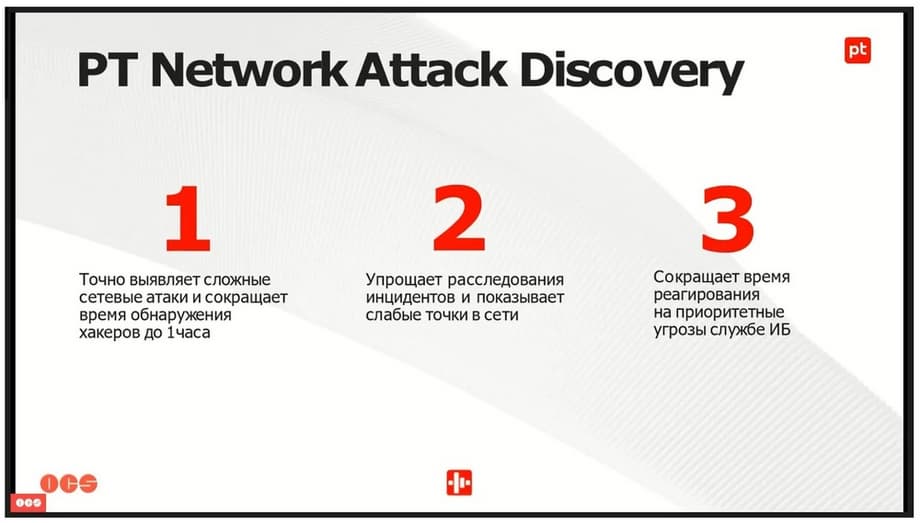
It allows you to accurately identify complex network attacks and, most importantly, it reduces the time to detect an attacker to approximately one hour.
PT NAD allows you to simplify incident investigation and show all the vulnerable points in the network. And it reduces the response time to priority threats to the information security service. So, how does PT NAD work?
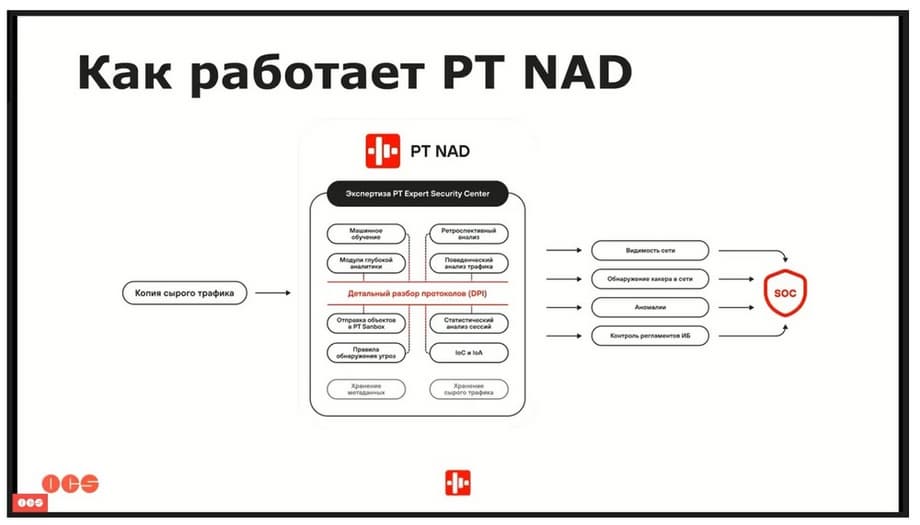
We submit a copy of raw traffic to the platform . This point is very important, because the more high-quality traffic we submit in terms of volume, the more complete picture we will see. Threat detection rules and IoC, rules and so on, and so on, DPI expertise, i.e. detailed analysis of protocols, if there are files in the sessions, they will be sent to PT Sandbox for verification. At the output, we get full network visibility, i.e. we see everything that happens in the network virtual live, the delay is from 3 to 5 minutes. All sorts of network anomalies, attacker tools, their movements, all their activities become apparent. Well, and also, importantly, PT NAD allows you to comply with the control of information security regulations. That is, we can observe compliance with the password policy through PT NAD.
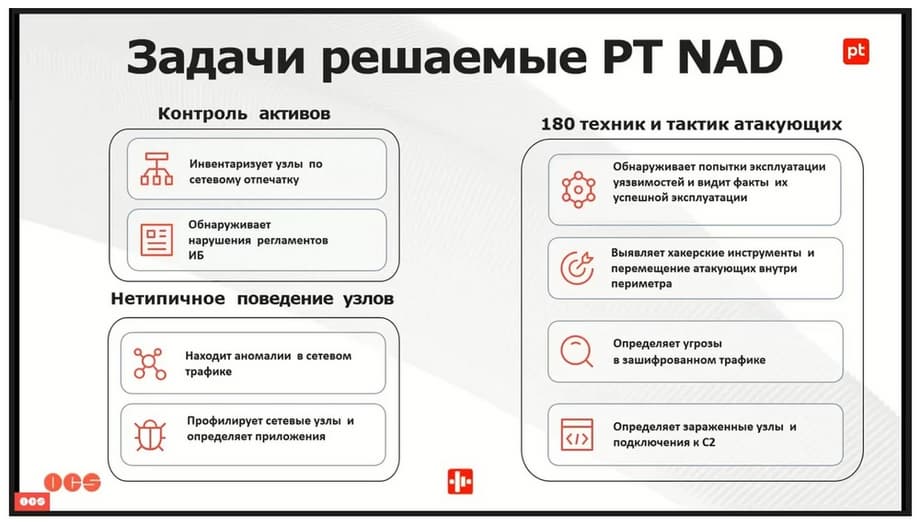
So, the main tasks that PT NAD solves are detecting violations of regulations and inventorying nodes by network footprint (i.e. even if the network node changes its IP address, PT NAD will be the same.), finding anomalies in network traffic, profiling network nodes and identifying applications. This function appeared not so long ago. Very useful, very convenient. And also, detecting attempts to exploit vulnerabilities and, moreover, what is very important, the fact of successful exploitation; identifying various kinds of hacker tools, attacker movements, communication of software with command servers, etc. That is, identifying threats in encrypted traffic. It would seem, encrypted traffic. But in fact, PT NAD has a number of mechanisms that can determine the malicious impact by indirect signs. Well, and determining connections to command servers and identifying infected nodes. These are the tasks that PT NAD solves.
The usage scenarios here are also quite extensive.
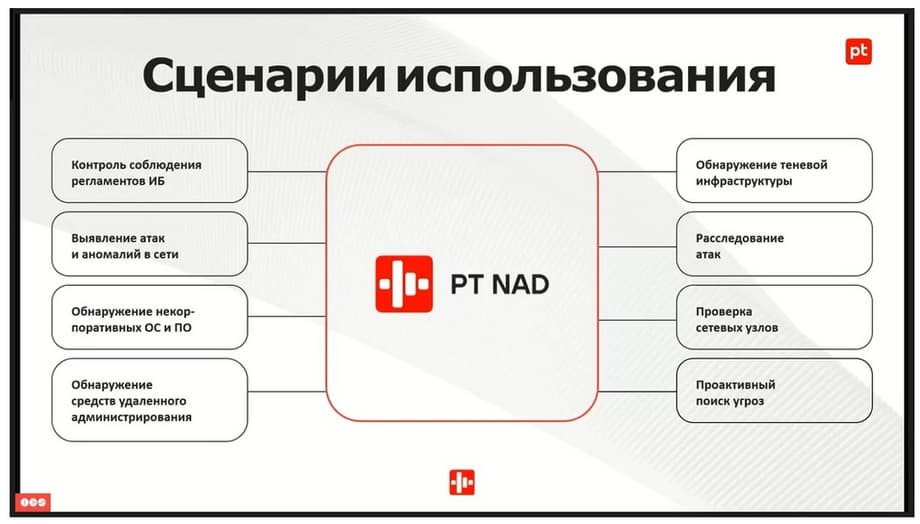
This includes investigating attacks and detecting shadow infrastructure. I had a case on a pilot project when one employee brought a computer from home. We then caught a lot of "triggers" from it. And we were lucky that the infrastructure was not encrypted then, nothing happened, and no one penetrated. But there was such a moment when security guards could not understand what happened, why there were constant network scans , where constant miners and other things were spreading from. It turns out that they found a home laptop in the infrastructure with the help of PT NAD.
Checking network nodes, detecting remote administration tools of various kinds, we also see this very well through PT NAD. Detecting non-corporate operating systems, detecting the same non-corporate software , identifying anomalies and controlling compliance with regulations. Also about active threat hunting.
Let's move on to the second component of our event today. This is PT Sandbox. This is a fairly good, convenient, very understandable and effective sandbox.

Detects malware at the hypervisor, operating system, and virtual machine level. It easily integrates into any infrastructure and controls the main channels for transferring files and links. PT Sandbox is very easy to install, just connect sources and configure them, you don't need to have any super qualifications in order to configure and connect all this. It adapts to the specifics of the business and provides protection against targeted attacks. That is, we can configure virtual machines in PT Sandbox for a specific customer, they are customized. You can upload your own images. The more the traps are similar to the working machines in the infrastructure, the more successful PT Sandbox will be.
How does PT Sandbox work?

In general, the mechanics of the sandbox are quite simple. The sandbox receives files from various types of sources. On the left, we have email, the main transmission channel. Next , objects from network traffic (ICAP). The same PT NAD, there are separate sources created for it. Frequently used storage. Very often on pilots, we look at the names of the storage in PT Sandbox. Any API integration, and you can also simply upload a file manually. Once in PT Sandbox, the file undergoes both static analysis and behavioral analysis, if necessary. For example, some ordinary txt file will not go into behavioral analysis , because it has nothing to do there, in fact.
Next, all this goes through traffic pre-filtering. This can also be configured to increase the performance of PT Sandbox, or rather, reduce the load on it, while not removing anything from the source at the output. We receive signals about the presence of malware in objects, blocking malware both in email traffic and in ICAP. Yes, we can now block via ICAP. Well, and threat research. The same threat hurting. In general, all this is very useful for the entire SOC, for the entire Security Operations Center, for all its objects.
So, what does PT Sandbox protect us from? Basically, the sandbox controls the main channels for transferring files and links.

Basically it's mail. We can work both simply in copy mode, which is not very effective, but you can see, and in filtering mode. That is, these are objects of network traffic, from virtually any system that works with network traffic, we can receive data. File storage and API connectors. These are the main channels we have. Manual file upload is useful primarily to security operators directly . Users do not use this often, but it also has a place to be.
So, PT Sandbox operating modes

PT Sandbox can simply detect malware, i.e. we connected various sources and receive results. Actually, we identify malicious software connections , hacker tools and some malware.
Blocking mode. This is mainly ICAP mail, it also works with API connectors. This has a slight impact on business processes. For example, if we take mail, then , by connecting it in filtering mode, we are likely to get a delay of 3-5 minutes in receiving emails. This will not greatly affect business processes, but it will significantly increase the level of security. Because we have blocking of all unknown malware, including Zero Day, blocking from hacker tools, delivery of messages to users of files without attachments. That is, for example, you can configure it so that if the attachment in the email was malicious, then the user will simply receive an email without the attachment.
Threat research. This is more of an aid to information security operators, information security specialists , SOC specialists who receive information on certain objects that enter PT Sandbox either through sources, or they themselves upload it there manually. This greatly reduces the overall time for threat research.
So, our main topic today is PT NAD + PT Sandbox = Anti-APT.

The synergy of these two products gives the identification of the attacker both on the perimeter and in the infrastructure, the identification of previously undetected facts of infrastructure hacking , some "triggers". Here, the retrospective works in both products. Well, and expertise. We have quite extensive expertise from Positive Technologies , which is updated regularly. And this greatly expands the possibilities for investigation.
So, Anti-APT schematically looks like this.
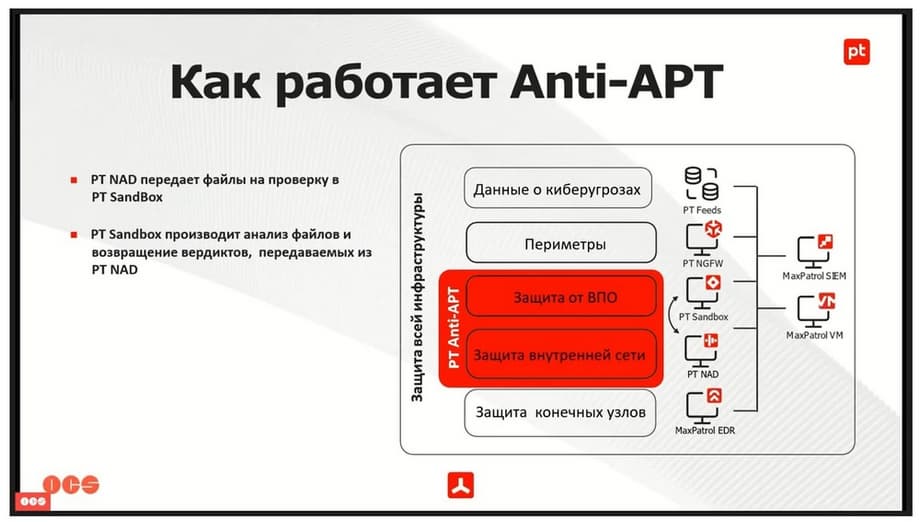
If we take the protection scheme of the entire infrastructure, take the main products, for example Positive, and here PT NAD and PT Sandbox have direct interaction. That is, PT NAD, finding files in any sessions , transfers them immediately for verification to PT Sandbox. PT Sandbox, conducting the verification, immediately returns the verdict. This is a very convenient, useful and effective tool.
Now let's talk a little about the capabilities of Anti-APT. They are quite extensive, but in short , this includes the detection of attacks by a large number of signs, and the reduction of the presence of attackers in the network, and protection against unknown and latest threats.

Moreover, since many of us are quite dependent on the requirements of regulators, our Anti-APT bundle allows us to close orders such as 239 and 21, and regarding GIS and ASUTP, these are 17, 31 and 489 orders of the FSTEC. This is important for many, both of our products have FSTEC certification. Everything is fine here.

Illustrations provided by the press service of OCS.
Now on home