Event of the special project of the "OCS Soft - PROdemo: Software Solutions Laboratory" team. At the meeting, we talked about the possibilities of using the vGate + ZVirt bundle and learned the principle of operation. Today's event is led by Evgeny Tarelkin, a leading expert at Code Security.
Today we will talk about the possibilities and nuances of using the bundle - a product called vGate from the company "Code Security" and a product called ZVirt from Orion soft.

Today we will talk about virtualization and its features in the current realities. We have a certain type of threats to the virtual infrastructure, because all serious attacks start with the desire to get into the virtual infrastructure.

It is quite difficult to protect the virtual infrastructure: large amounts of network traffic significantly limit the possibilities of the approach. In addition, we see that many IT services have come to love VMware products. And this is understandable, this product has performed well over the past decades and has become a kind of standard in the industry. But at the same time, since 2022, we have not had any updates from them. We understand that an attack on the virtual infrastructure leads to the IT infrastructure "lying down" seriously and for a long time, pressure on virtual machines leads to their deletion and deletion of all their backups. We see many public and non-public stories when the infrastructure goes down for a day or two, or even three days.

In addition, we understand that many are required to comply with various presidential decrees on migration to domestic infrastructure and ensuring protection. These decrees are caused by the need to protect infrastructure, critical infrastructure of financial and other organizations. Because the same VMware products have certain critical vulnerabilities, and there are quite a few of them. And all our critical infrastructure, everything that the state wants to protect, is drawn into domestic virtualization, which is updated and developed.
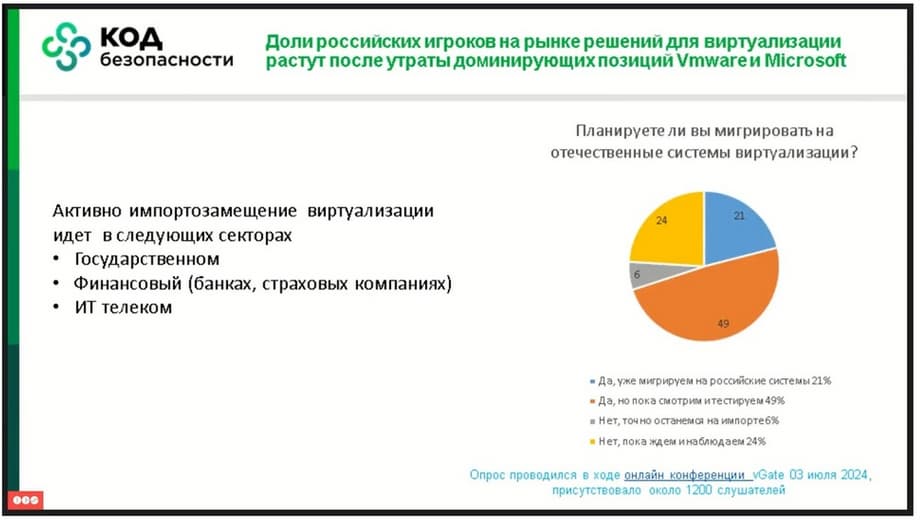
Therefore, we will talk about segments. As you can see, the main segments are just those segments where there are domestic organizations, these are government bodies, these are financial bodies, where any vulnerabilities are extremely critical and extremely expensive. And, of course, this is Telecom, an important part that is now actively developing, and domestic data centers now want to become an alternative to foreign ones. In July, at an event dedicated to the announcement of the new version of vGate, where 1200 listeners were present, we asked them how many people were ready to migrate. And we saw that migration is active, but at the same time there are some doubts among customers who are testing, choosing, and watching. For some, this is a mental fear caused by distrust of the domestic manufacturer. Moreover, it is often caused by certified versions, which impose certain restrictions on functionality.
Here, in fact, the vulnerability about which the FSTEC sent a letter. This news was published on Tag Advisor, and can also be found on Yandex.
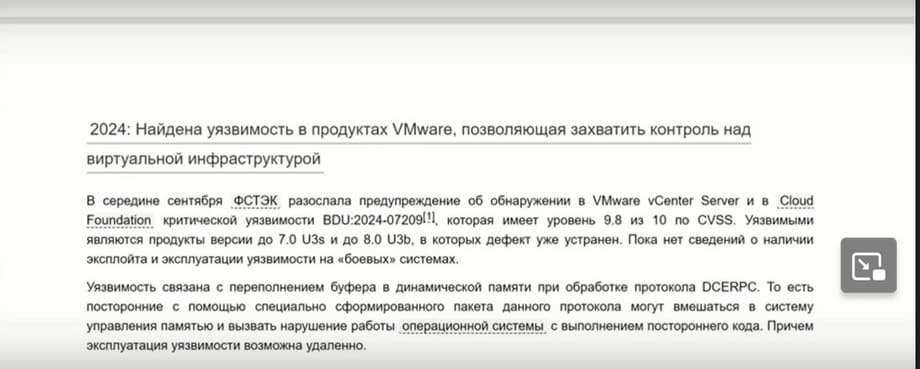
The vulnerability is really good and most customers are starting to take it very seriously.
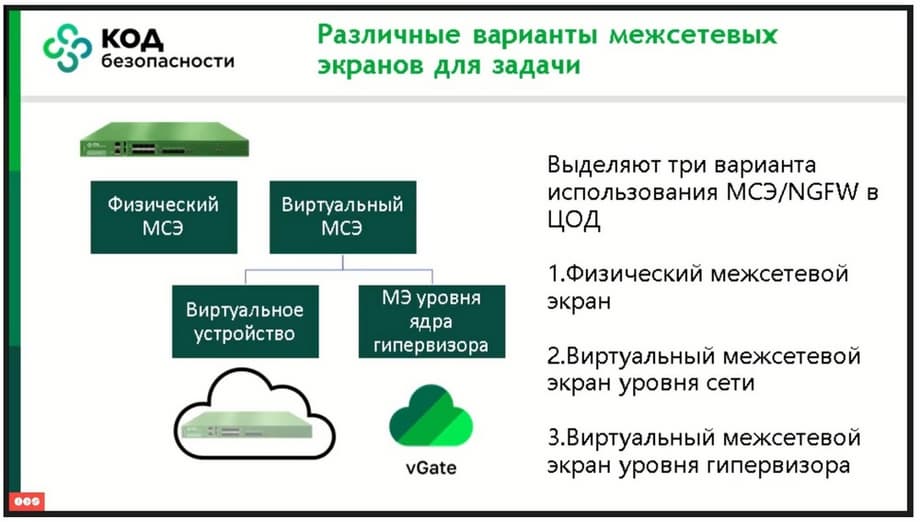
So, what is vGate? vGate is a platform for protecting domestic virtualization, and not only domestic, because we are compatible with VMware. But today we are talking about integration with zVirt, because zVirt colleagues are the most active on the market at the moment, and according to the results of 2023, they already had a quarter of the market, and, as far as I know, they have good ambitions to capture an even larger part of the market.

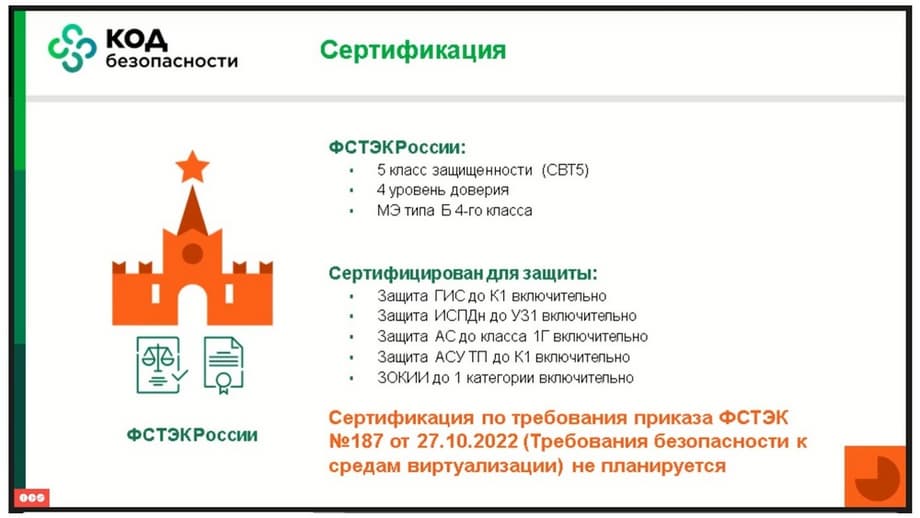
What can vGate do? vGate is a virtualization protection platform. Why do we need colleagues zVirt? Many of their customers say that they want more functionality, that they are used to VMware, and it is clear that we need to strive for this. But developers are finite, and the resources with which this can be achieved in a short time are limited. Therefore, there is simply no time left to build secure solutions. It is clear that the FSTEC requires the use of a certified secure solution in critical infrastructure, and the use of non-certified solutions there is highly undesirable, because they do not have the necessary security. But vGate has a solution for protecting information as an imposed tool. And it allows you to pass certification even for a non-certified version.
We offer a joint solution, where the non-certified version of zVirt offers all the functionality available to date, i.e. all new versions that are updated quite often. vGate acts as a means of protecting this virtualization, i.e. precisely as a means that protects both from the point of view of managing virtual machines and from the point of view of network microsegmentation. Because we have a network protection solution in the form of a firewall, which is certified by the FSTEC.
The joint bundle provides protection for the virtual infrastructure. Why is this needed?

An attack on the virtual infrastructure is perhaps the main goal of attackers. And at the same time, we see a large number of cases that have become public.
Here is a very recent case. Attackers erased all virtual machines, backups, etc., it was a very serious attack. This was written about on RBC, the infrastructure was restored for several days.
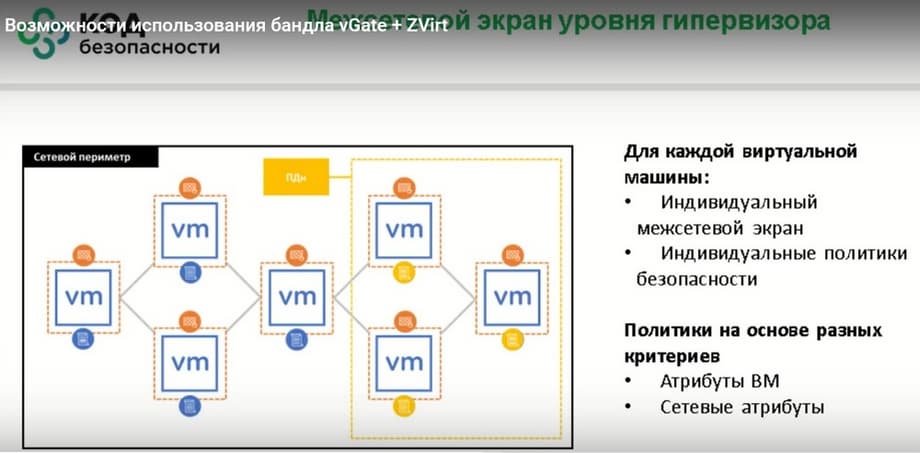
What do we offer? First of all, this is microsegmentation. This is a solution for dividing the infrastructure into separate small sections. Perhaps one of the best examples of this can serve as firebreaks that are made in forests. Forests are divided into separate squares so that the fire cannot spread to the neighboring segment. That is, it becomes isolated in this segment. And all the actions of the attacker are either minimized in this square, or, when they jump to neighboring squares, they subside. Thus, we reduce both the probability of an incident and its severity.
Why is this needed and why is this important?
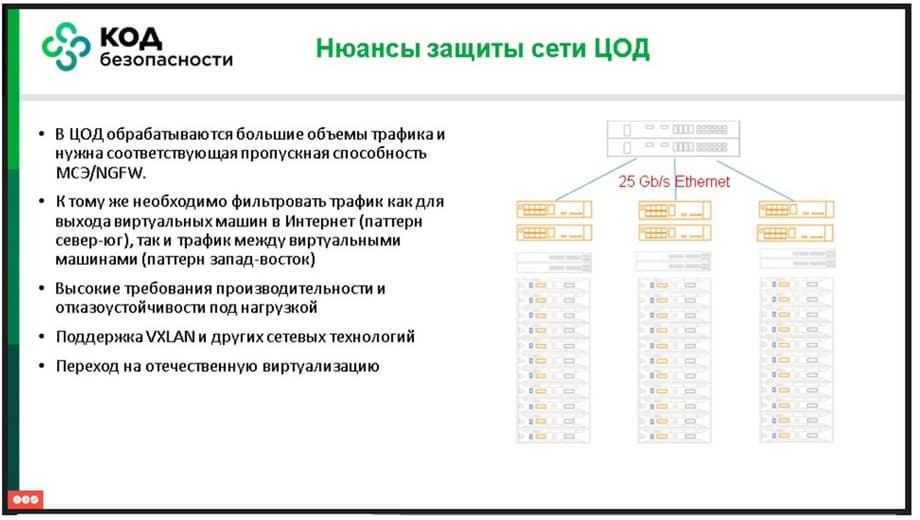
To date, our IT infrastructure consists of servers that use at least 10 gigabits. This is not so much a standard, the standard is still 25, but at the same time there is still a solution that uses 10 gigabits. On a good server, we have 2 by 25 gigabits, and on a high-performance server, which does not use everything on the third generation, but at least something new, and even if it is the sixth generation, where there are several hundred cores in one server, it is clear that 2 by 25 is already not enough, and therefore 4 by 25 is already used there. It is clear that all traffic is inside, and about 20% comes out to the top. Why is this needed? The main load is migrations, backups, processing. Somewhere the virtual machine just moves from one physical server to another, somewhere it tries to get more resources. That is, there are many tasks. Machines move, and it is clear that the traffic is large, because if we take even 50 gigabits from each server, and we have, say, at least 50 servers, then we already get quite large values. And if we have 100 gigabits and 100 servers, or even 200, then the value becomes quite frightening.
How are customers protected in such cases from such attacks? The answer is actually very simple and unexpected: not at all! Because there is a lot of traffic, and it is quite difficult and expensive to close it with standard hardware firewalls. Here, a certain restriction is imposed, because the physical firewall is an additional element that needs to be placed in cabinets.
Plus, we understand that the exit of traffic from the virtual environment to the physical environment is a delay. We understand that the physical firewall is an additional entity that lives, has an operating system, and there are even more delays. And for database tasks, web applications, all this imposes a certain delay and is very sensitive. It is clear that all this can be slightly reduced by using virtual appliances. But, still, this is a virtual machine, it is not so sensitive to performance, because it uses the virtual resources of the host where it is located, it is not so limited, but at the same time we understand that it cannot scale like that. That is, if you give more cores and more memory, this does not always lead to an increase in the performance of this virtual appliance. At the same time, we understand that delays also occur in this device, because it is the same entity, in fact, from the same operating system, except that the traffic does not go to the physical level. Someone says that they will do segmentation at the level of physical switches. This can also be done, but here there is a certain limitation from the point of view of going to the physical level, plus there is a certain limitation on the amount of megabytes in the switches.
And the most, probably, high-load task, it is more related to information security, is when a virtual machine moves to another IP, to another physical server, and we need to manually rewrite the filtering and traffic rules. This imposes a certain restriction on the performance of information security employees, when there are many virtual machines and few employees. And they either do not have time to do all this, or they do it with some delay, which leads to certain vulnerabilities. If we are talking about a hypervisor-level firewall, which is in vGate, then it is carried out due to traffic filtering precisely at the hypervisor level as such, that is, it does not have any delays, it uses the virtual network card that is at its disposal, and does not introduce any additional delays, thereby greatly simplifying the infrastructure.

It is clear that there are large solutions at the level of the data center switch. We have a 7-unit firewall, it has several blades, there are balancers, there is a 100-gigabit interface. But at the same time, its cost will shock you. It is clear that this is really the level of a very large data center. At the same time, its performance is limited, i.e. the granularity is quite high. When you need a little more, you need to buy several such pieces of iron. And over time, when the number of servers grows, we understand that the number of cores, network load, and performance of the hardware firewall do not increase. And all the settings that are created in the firewall of this level, they are created at the level of the start of the virtual machine. That is, the virtual machine already starts with the rules that we have prescribed for it. It is automatically deployed with filtering rules. And when it moves, all these traffic filtering rules remain attached to this virtual machine, we don't need to change anything.
Thus, we significantly reduce the load on those colleagues who write these rules for firewalls. We spoke with customers, conducted surveys. Let me remind you about our study that was conducted by us in July. All 1200 listeners who attended the seminar, when we asked them about the need to use microsegmentation in their solutions, told us how important it is for them.
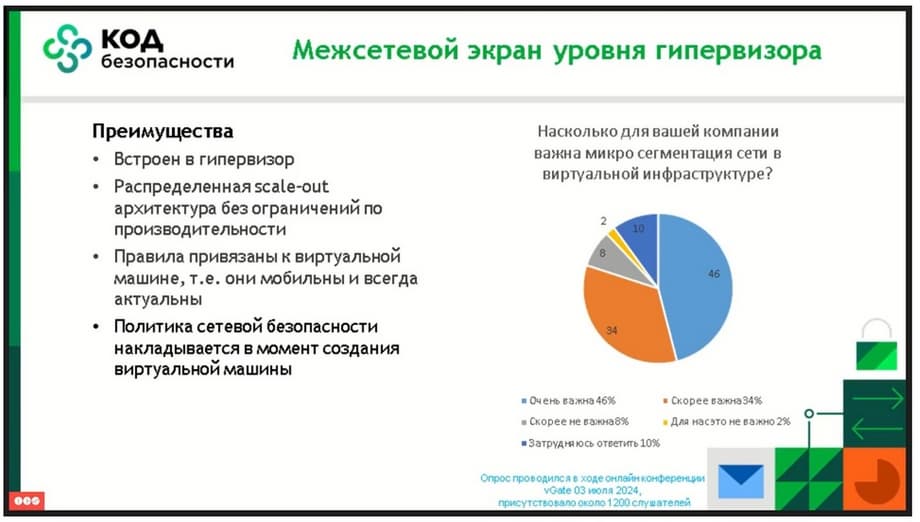
And almost half said that it is very important for them. And another 34% said that it is simply important. That is, 80% of listeners said that this is an important solution for them. This means that customers in their majority understand why this technology is needed and how to use it.
We have been making the firewall for several years. There are successful applications where more than three thousand processors are deployed, that is, 1500 servers and tens of thousands of virtual machines. The solution has shown its performance and efficiency. There are similar cases, and the cases are different. There are also 70 servers, 30 servers, and one and a half thousand. We have an FSTEC certificate. Our company is the only one on the market that has such a certificate.
What is the main interest of customers? In addition to convenience, there is also an economic component, which says that if we calculate the traffic filtering, we will take the classic device on md4v and in the firewall mode we will calculate the number and compare the cost of LIDI licenses as a software solution at the hypervisor level, as well as with hardware solutions.

And even with small installations on a 10 GB/s interface, the difference will be threefold. With large installations with a 25 GB/s interface, it will be very large and reach up to 10 times. As I already said, the level of filtering on the physical firewall is quite difficult to scale.
What is the advantage of our integration with vGate in the form of a bundle? First of all, this is guaranteed compatibility.

We work very closely with our colleagues. Our development departments jointly promote solutions. And we see in advance all the versions that are released. If we are talking about certified versions, they are significantly behind in functionality, because the certification of the same zVirt takes a lot of time. The certified version is released with a delay of 12-14 months. We are talking about a difference in versions of 1-2 months. Now we want to reduce it even more, that is, within one month, our development team synchronizes, and all versions will be added to the form, which will allow us to provide the customer with the most functional product. Roughly speaking, the customer will receive all the functionality that zVirt offers at the moment, all new versions. At the same time, we, as an imposed tool, give the opportunity to pass certification. We are talking about a single technical support, that is, the grouping of their technical support is provided by zVirt colleagues. By purchasing the bundle, the customer comes to zVirt, and they answer all the questions there. Engineers at zVirt know the vGate product. In case of complex questions, they transfer them to our technical support, but still answer through the zVirt channel. For customers, this is much easier. Thus, we are saying that information security and IT become in the same row and go together. And, if earlier the certified version from zVirt pleased information security employees, they received a certificate, but information security, showing this certificate, told IT specialists that the product, of course, was completed with a delay of 12-14 months, and it does not reflect the latest trends in functionality. But now, in the form of an imposed tool, the customer receives both the latest version in terms of functionality and the corresponding requirements of the regulator. Thus, we go hand in hand and support the interests of both.
Illustrations are provided by the press service of Code Security
Now on home

Герой России Гарнаев: никто из профессионалов о возобновлении производства на КАЗ всерьёз не говорит

Система отслеживает спутники на высотах до 50 000 км и ведёт за ними наблюдение

The armored vehicle is equipped with a KamAZ-740.35-400 diesel engine with a power of 400 hp.

Constant improvements in avionics, weapons and tactical capabilities will make the aircraft a flexible response to future challenges

The exterior of the KamAZ-54901 features fairings on the cab and chassis for fuel economy

Fighters are in demand both domestically and abroad

Tyazhpromexport and Venezuela Agree on Plant Revival

The company not only completed the state order, but also quickly mastered the production of AK-12K for special forces

Experts have developed a photogrammetric complex with a resolution of less than 1 cm


