Today's program includes: • Overview of the new USG FLEX H series; • Comparison with ATP and USG FLEX series; • New OS and its features; • Configuration examples. Today's Zyxel event is dedicated to the new USG FLEX H series of firewalls.

In fact, these devices have not yet started to be actively sold because these firewalls have a new operating system and functionality that is available in the current lines, not all of which has been implemented.

The features of the new USG FLEX H series are a new OS and port flexibility for all models; all ports are configurable; any port can be configured as LAN or WAN; some models, starting with the 200 series, support Gbit. Some models support PoE.
Performance has increased by approximately 3 times compared to similar models. USG FLEX is currently only monitoring without management. We have not yet decided "which way to go," either to make it like the USG FLEX series, i.e., two operating modes: either a full configuration mode with a stripped-down web interface, or a monitoring mode where the web interface remains fully functional.
Next is the new VPN client - "two in one," because it now supports not only IPsec, but also SSL-VPN.
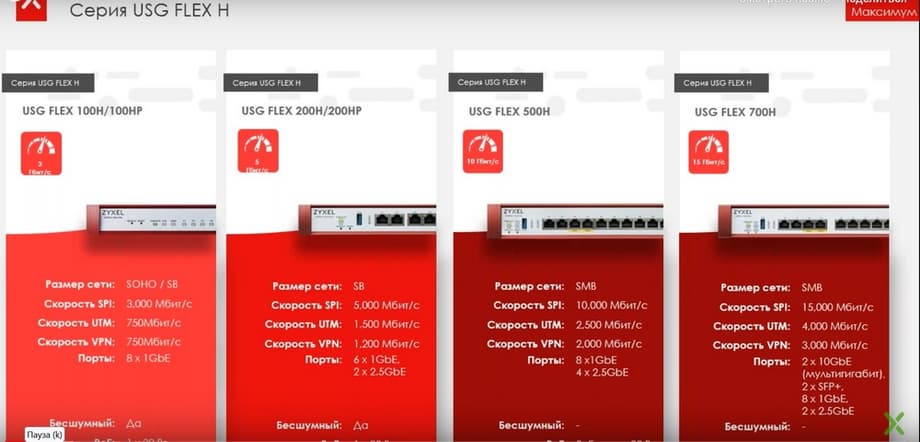
The slide presents 4 models of firewalls, there are 6 in total, there are also models USG FLEX 100H/100HP and USG FLEX 200H/200HP, with PoE support. The 500th and 700th models already support PoE. On the slide, you can see the performance and the number of ports of these devices. Starting with the 200th model, there are two multi-gigabit ports at 2.5 Gbit, in the 500th model - 4 such ports, and what is in the 700th model, you can see on the slide.
The next slide shows the top model.

The first two ports are 2.5 Gbit, the 3rd and 4th ports are 10 Gbit with PoE support, then there are gigabit ports, and then two more ports on SFP+ 10 G.
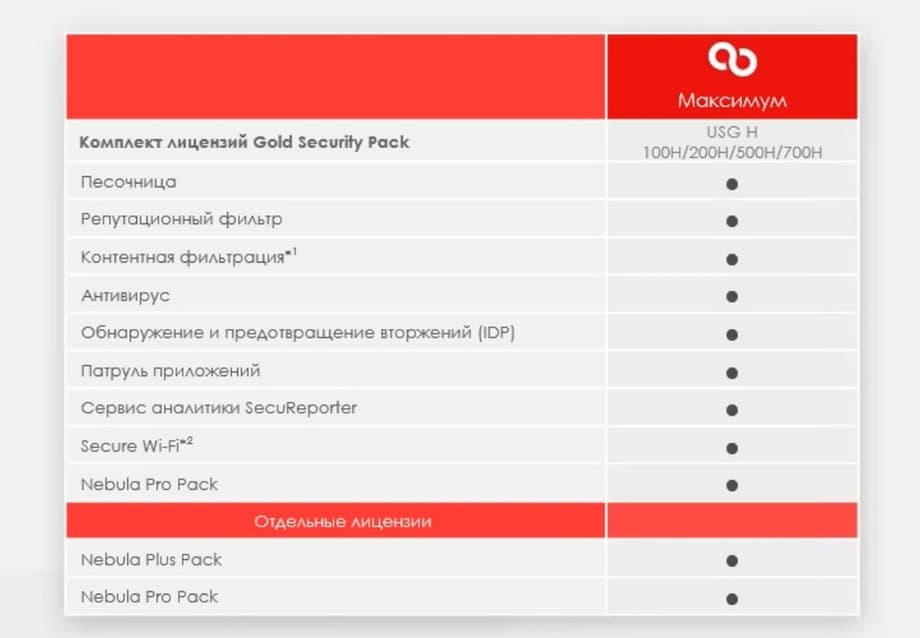
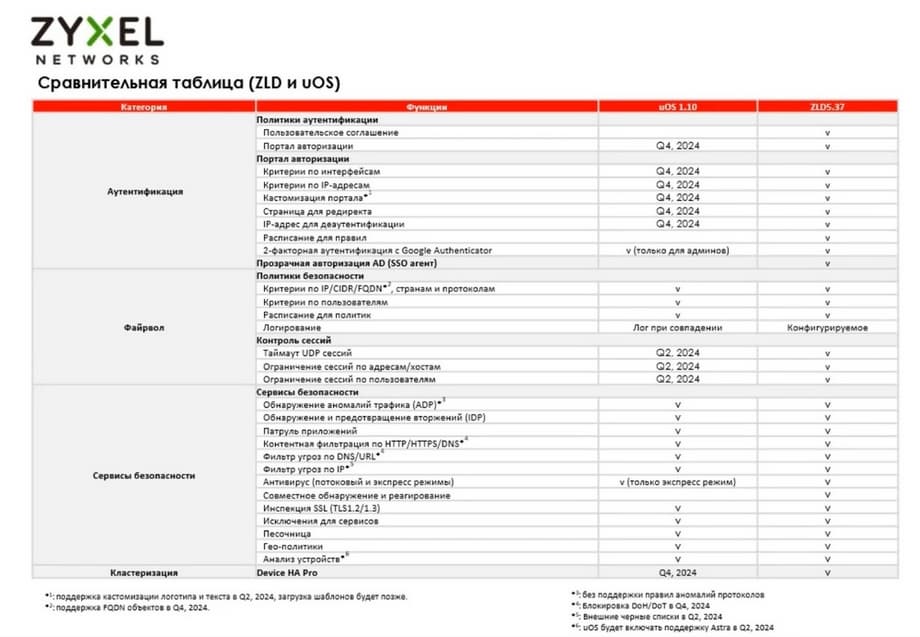
For this series, there is a Gold Security Pack license and a separate license for Nebula Pro Pack. The Gold Security Pack also includes Nebula Pro Pack and all other UTM services: sandbox, reputation filter, content filtering, antivirus, etc. Secure Wi-Fi is not yet included, as there is no support for it yet, it will appear later. And content filtering currently does not support operation in Russia and Belarus.
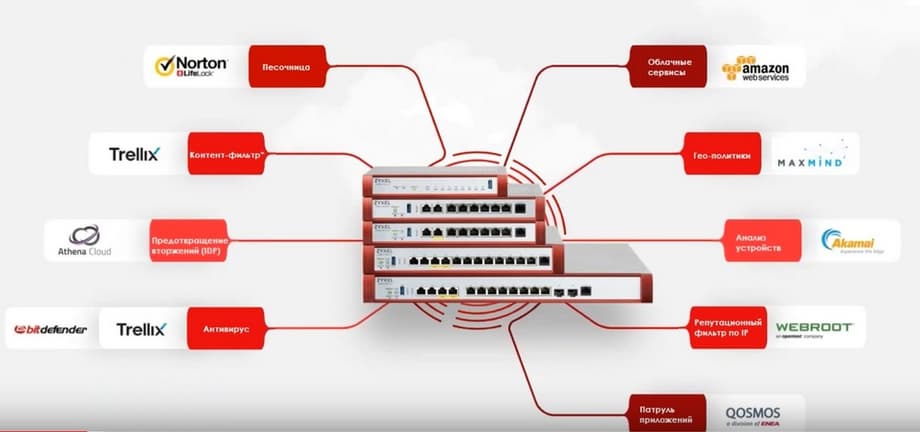
The slide above shows the services provided by UTM.
The main distinguishing feature is the new operating system - uOS. It is designed to improve security, minimize system response time, instantly apply changes, and optimize configuration management through a new intuitive design.

The advanced system panel has navigation, the menu structure hierarchy is available at the top, you can select different levels there, there is support for the "favorites" function, you can add the necessary menu sections that are used more often, there is a menu search, an object search, a keyword search. The DPDK architecture allows you to achieve maximum performance through FastPath technology, and migrating to other hardware platforms has become easier compared to the previous version. The new graphical interface provides a better overview for monitoring and statistics.
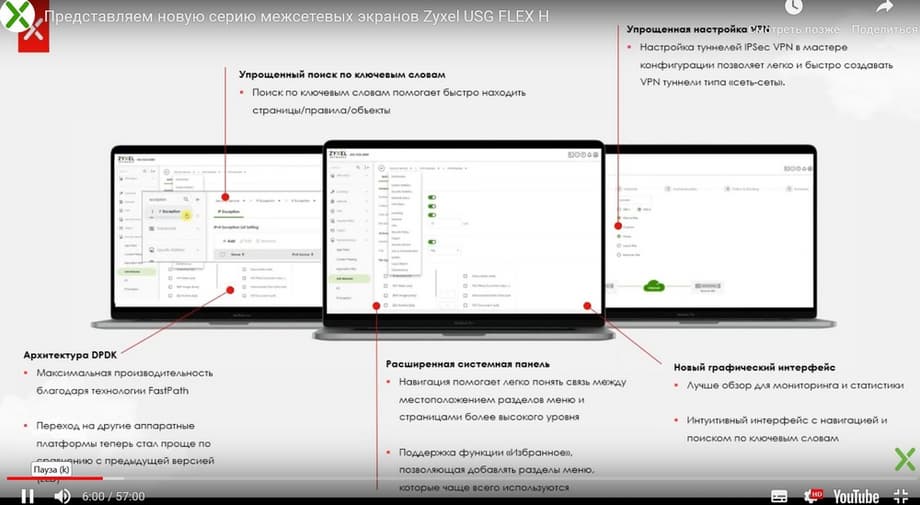
The DPDK architecture can subsequently be used on other hardware platforms.
Next, let's compare the current uOS operating system with ZLD. This comparison can be seen in the following table. In short, the access point controller, automatic change of their power, as well as the detection of other access points and port aggregation, all of this will only appear at the end of 2024.
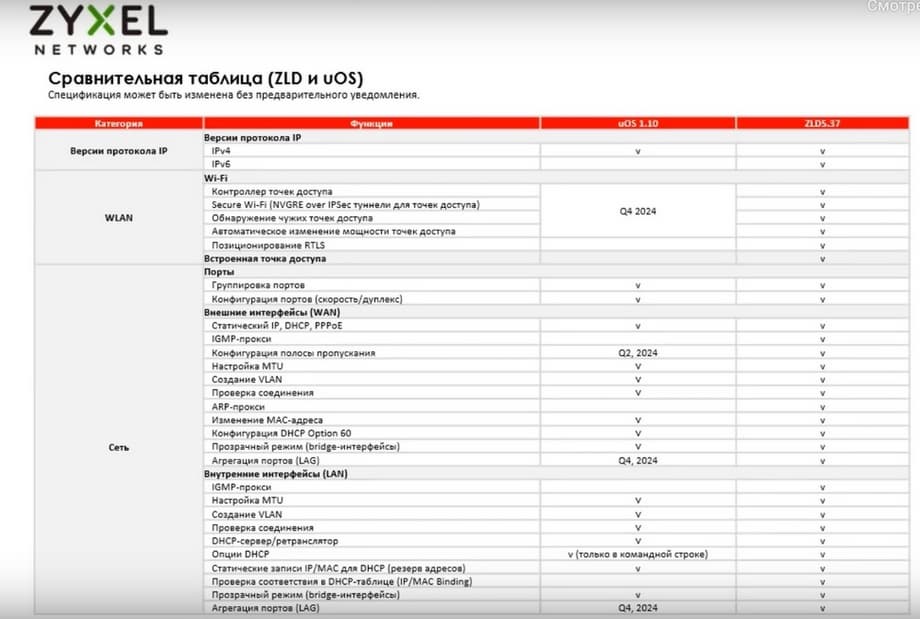
And the configuration of the bandwidth of external interfaces will be available at the end of the second quarter of 2024.
The new uOS (USG Operating System) operating system is a DPDK architecture with FastPath technology support (or kernel bypass). Here, all models are multi-core, and part of the processor cores will be reserved only for traffic processing, and the remaining cores for other purposes.
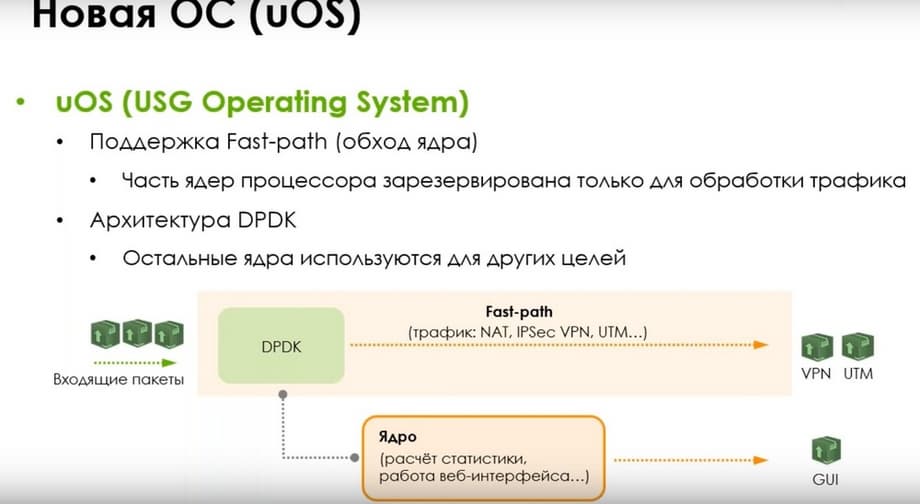
When incoming packets arrive, if the traffic goes past the kernel and packet processing passes past the kernel, this increases performance, and the kernel at this time is engaged in calculating statistics, initial session opening, and web interface operation.
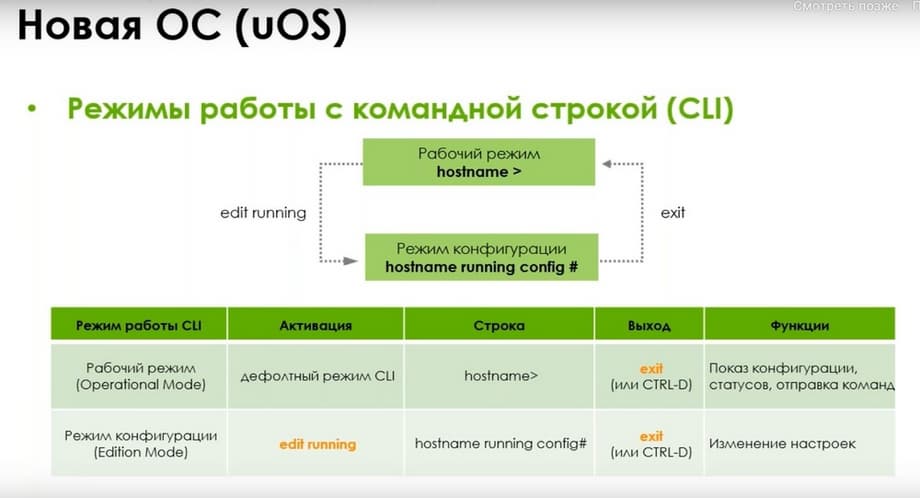
The command line operating mode is different, and to enter configuration mode (hostname running соnfig), you need the edit running command, which is necessary to change settings. To exit this state, you can enter the exit command or press the CTRL-D keys.
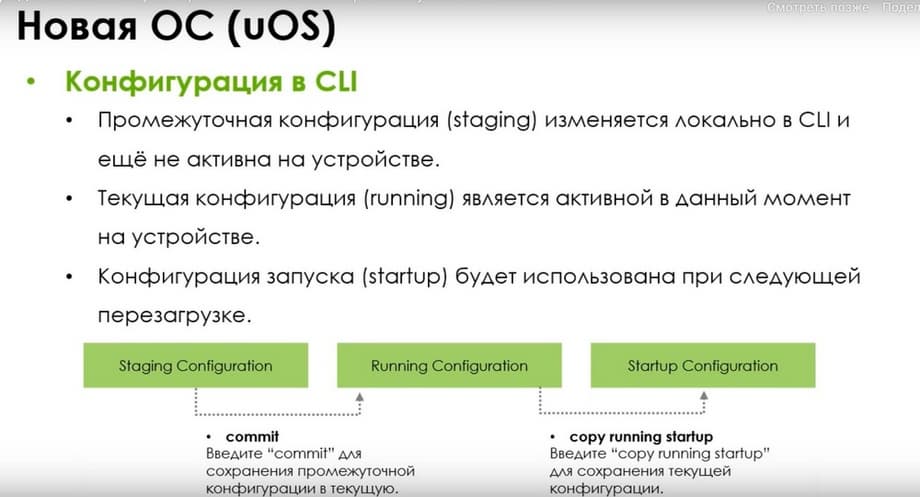
The configuration in CLI also differs, there is also an intermediate configuration (staging) that is changed locally in CLI and is not yet active on the device. The current configuration (running) is active at the moment on the device. The startup configuration will be used at the next reboot.
Enter the commit command to save the intermediate configuration to the current one, and enter the copy running startup command to save the current configuration.
This cannot be achieved through the web interface.
Indicators and buttons
A REBOOT button has appeared, which can be used to reboot the device. The RESET button is for resetting the configuration.

There are PoE indicators for models that have such support. There is also a USER indicator, which can be used for your own events; this indicator is pre-configured and can be activated to light up green when the administrator logs in, light up amber, for example, if one of the users is blocked, if they entered the passwords incorrectly, or blink green if the license has expired or a new firmware is available.
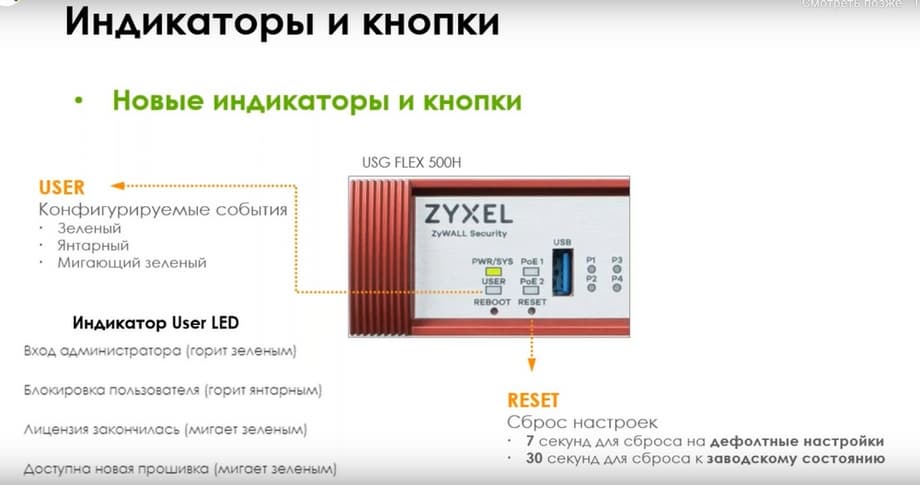
A button for resetting settings; if you press and hold it for 7 seconds, the gateway will reset to default settings, and if you hold it for 30 seconds, the settings will revert to factory state.
Working with Nebula
The system will work with Nebula, and at the moment this will be an analogue of the monitoring mode for the current lines, so at the moment the functions are visible on the slide.

This is the device status (online/offline), reboot, remote access to CLI (SSH) and remote access to the command line and web interface, firmware update, configuration backup (including on a schedule) and uploading it to the gateway, license management. Even if you have blocked ports 443, 70, and 23 for security reasons, you will still be able to access Nebula.
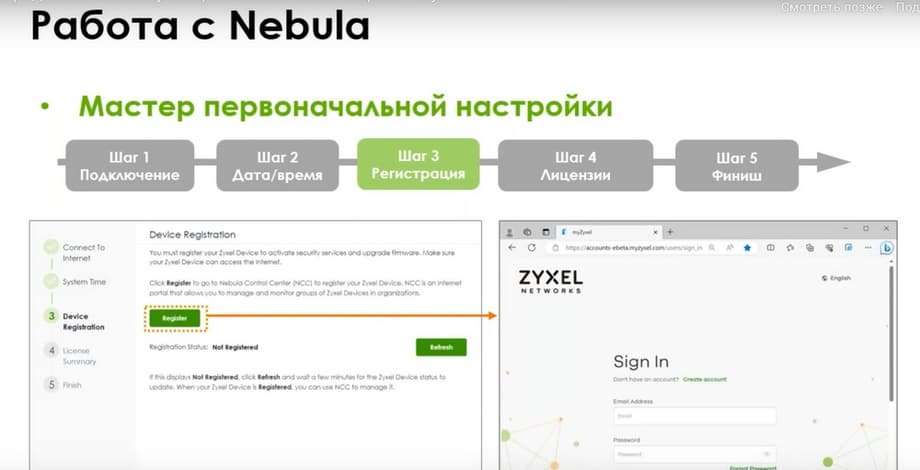
Firmware update, configuration backup, including on a schedule and application on the gateway, and license management. I.e., in the current line, they are mainly managed now through the myZyxel portal. There you register the license. Although this can also be done through Nebula. I.e., Nebula will completely replace the myZyxel portal in the near future. Both adding devices, registering licenses, and linking the license to the device, all of this will be done there. And if you go through the initial setup wizard on the gateway, then when you click on the registration button, you will be directed to the Nebula portal. To log in to Nebula, you can use the same account as on the myZyxel portal. After that, you specify or select one of the organizations and sites. And add the gateway to this site.
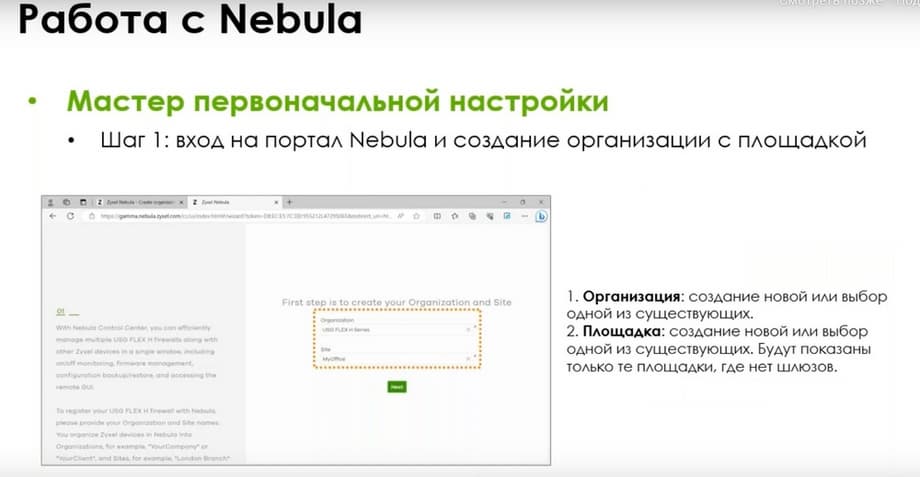
If the device registration is skipped, then when you log in to the web interface, the device status will be displayed as unregistered. And a window with a QR code will appear, which can be used to register Nebula using a mobile application. If you do not have a mobile application installed yet, the QR code will redirect you to the application store.

The Nebula organization site with USG FLEX H will also automatically create the same organizations and sites in SecuReporter during device registration. I.e., when the gateway is assigned to a site, Nebula immediately informs SecuReporter. Therefore, you will not need to add it separately to SecuReporter, it will be there immediately. If you register the gateway on the myZyxel portal, not Nebula, it will not be automatically added to SecuReporter.
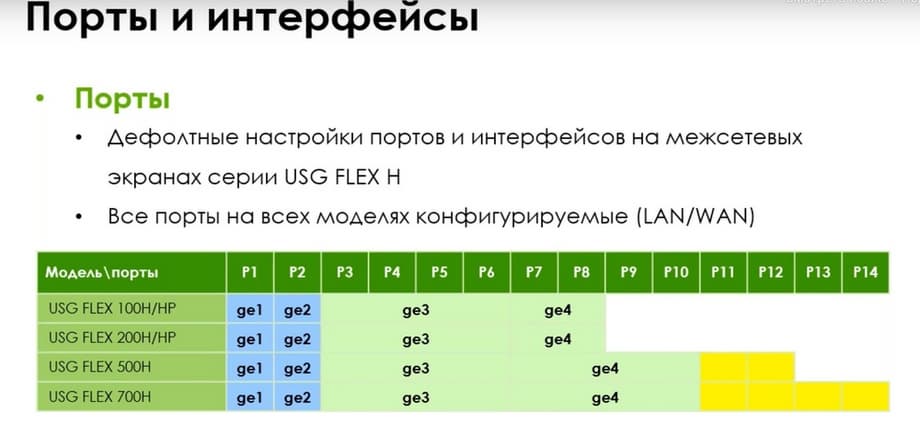
All ports on all models are configurable. You can assign them as LAN or WAN. But at the same time, there are still default settings. The first two ports are usually WAN, the external interface. Then, you see, there from the third to the eighth or tenth ports - LAN port. The rest are optional.
I repeat, that any port is configurable, and you can configure it as an external interface or an internal one. Ports can also be grouped. But at the same time, some models have individual ports that cannot be added to groups. These individual ports are not connected to the chip-set and switch; they are connected directly to the processor. Therefore, they cannot be added to groups. But at the same time, the traffic processing speed increases.
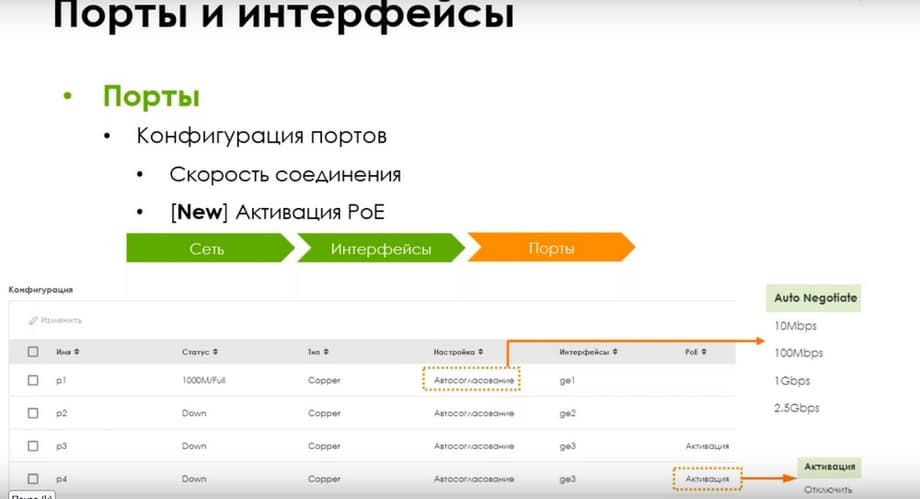
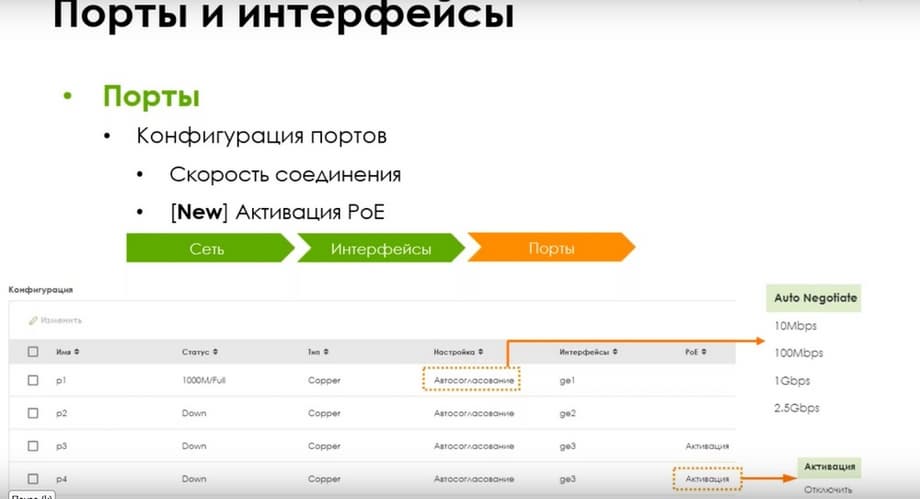
Regarding the port configuration. The connection speed is available in the current lines. But since there are PoE models, there will be an opportunity to turn PoE on and off on ports with support. At the same time, the total budget is 30 W on all models.
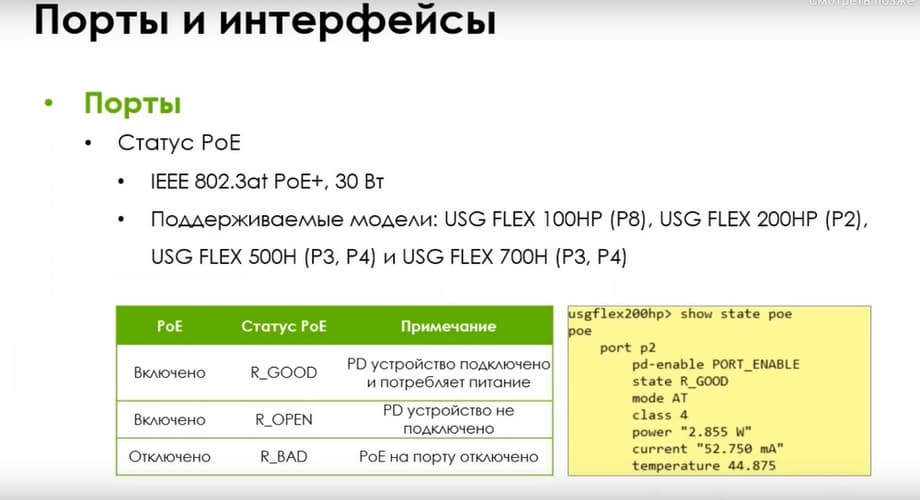
I.e. this is the maximum budget, and depending on the model, there is one port or two ports with PoE. You can view the PoE status through CLI. As you can see, there are 3 PoE statuses here: R_GOOD, R_OPEN, and R_BAD. Accordingly, R_GOOD is when the PoE device is powered, connected, and consuming power. R_OPEN is when it is not connected, and R_BAD is when PoE itself is disabled on board.
The interfaces in the current lines also have internal, external, and general ones. But general ones can only be configured through CLI.
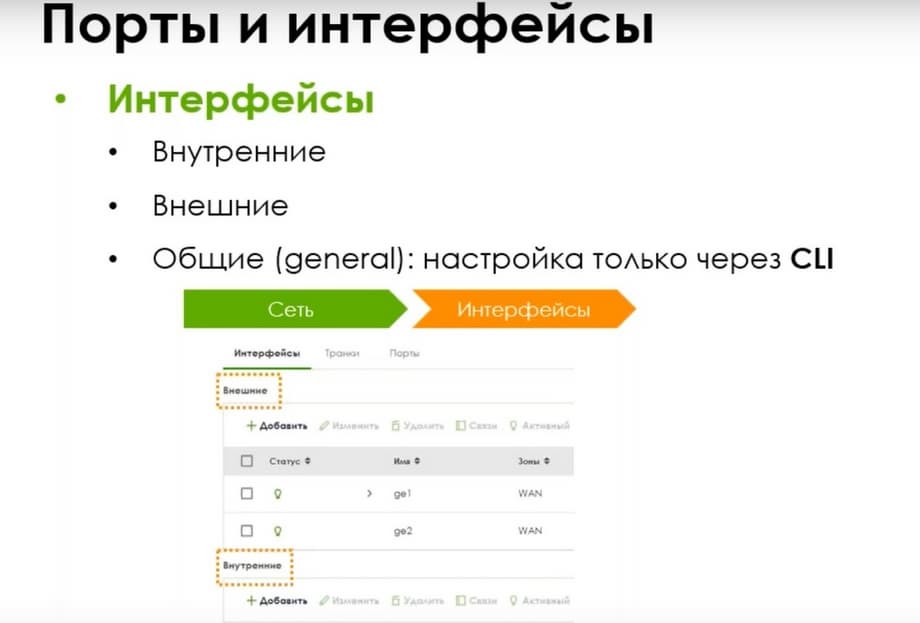
I.e. in the web interface, you will not see a section with general interfaces until you create at least one general General interface through CLI. And after that, they will appear in the interface. And initially, there are external and internal interfaces. The configuration will not differ in any way, except for the case if your provider uses PPPoE, then it will be configured immediately on the external interface.
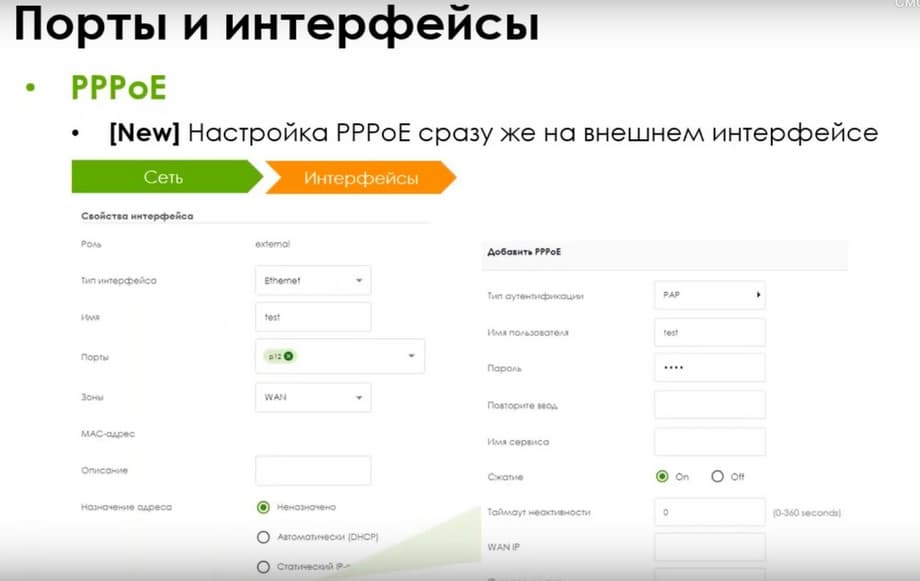
I.e. you do not need to create another interface as in the current lines, but you can immediately specify that it uses PoE when creating the interface.
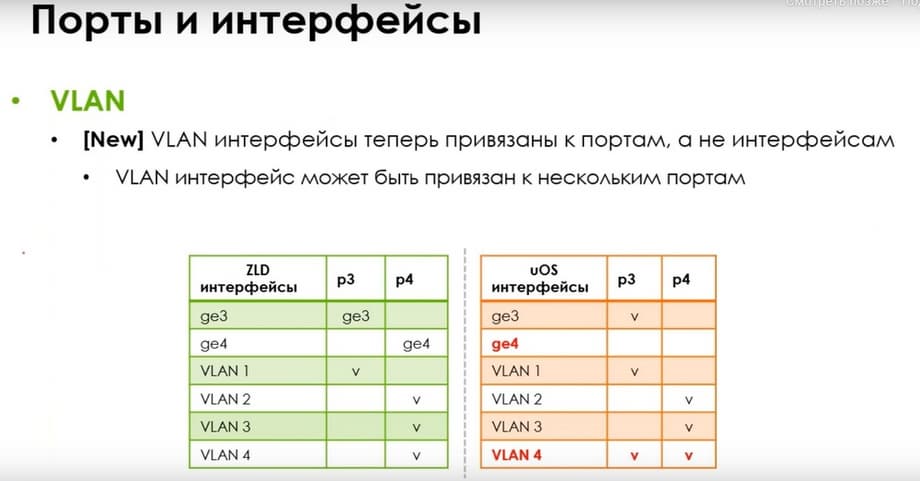
VLAN interfaces. Their configuration also differs from the current interfaces. If now they are tied to interfaces, then now VLAN interfaces are tied to ports. And a VLAN interface can be tied to several ports at once, regardless of the current interfaces. I.e., VLAN interfaces are now not related to logical interfaces ge3, ge4, etc.

Bridges are also available. Let me remind you that they consist of several interfaces and work as L2 switches. Packets transmitted between interfaces do not change the MAC address. At the same time, on the interface that you add to the bridge, you need to remove the IP address, i.e., you can simply check the box "without assigning an IP address." And the routing function will not work for them. Traffic passing through the bridge is also checked by the firewall and UTM services, as in the current lines.
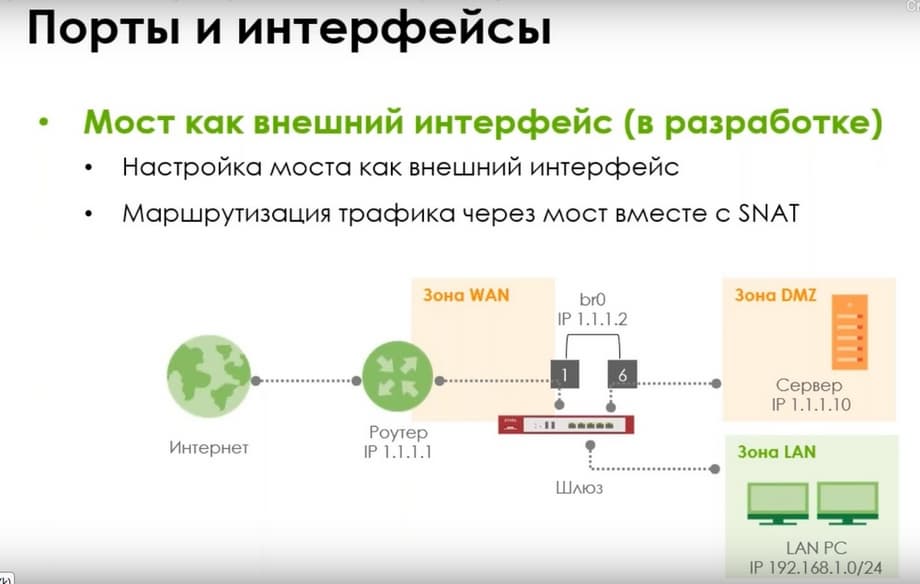
The Bridge as an external interface cannot be used yet (it is under development). It can only be used for traffic forwarding for now. And it cannot be used as an external interface together with SNAT yet. This development will appear later in the following firmware. Let me remind you to which zones the traffic through the bridge belongs. It belongs to both the interface zones and the bridge zone. And if, for example, the WAN interface and the DMZ interface in the corresponding zones are added to the Bridge zone, then the policies such as WAN to DMZ, Bridge to Bridge, WAN to Bridge, Bridge to DMZ will fit. I.e., any ethics from to these directions will fit. And accordingly, LAN to DMZ, LAN to Bridge will also fit. You can use either one or the other direction to create rules for working with traffic.
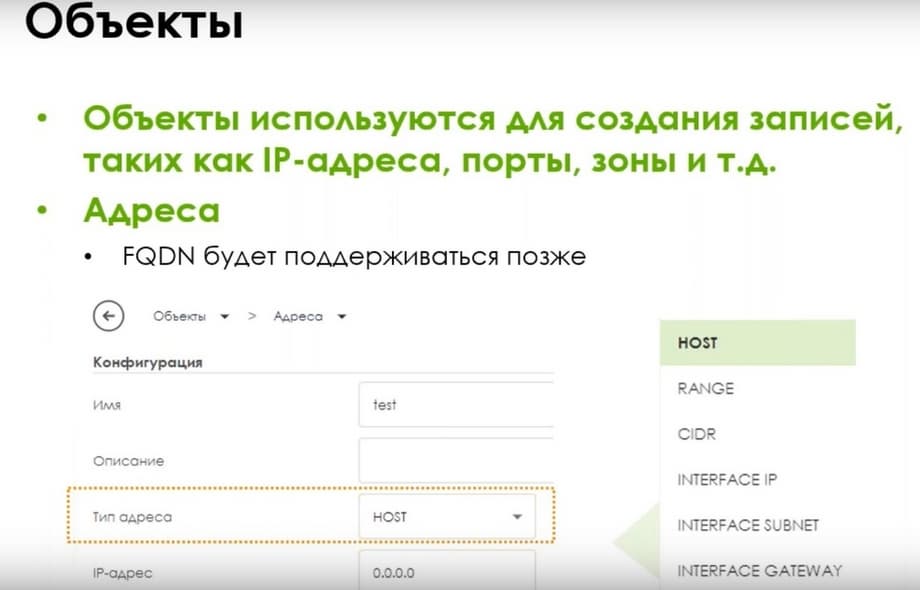
Let's go through the objects. There are no particular differences in how they were and are in the current lines: IP addresses, ports, zones, etc. The only thing is that FQDN records are not supported yet. This will appear later. And now, when creating any rules, routing policies, security policies, you can easily operate on objects immediately. You do not need to jump between different menus, objects, and policies. Now, when creating any policies, as soon as you click on the source, you immediately have a choice of addresses, objects, and you can immediately add either a new object or a new letter. And if you need to change the current object. Now you can do this immediately, without going to the object section.
Now on home