A joint event by OCS, Astra Group, and Digital Technologies focuses on securing the perimeter using Astra Linux OS tools. Speakers discuss setting up a workspace for electronic signatures and secure document exchange using Crypto ARM GOST and CryptoPro CSP. Speaker topics include: "Securing the Security Perimeter with Astra Linux OS Tools" and "Features of Installing, Configuring, and Operating Cryptographic Tools on Astra Linux Special Edition."
Today's speakers: Maxim Kurtin, Deputy Director of the Information Security Department, Astra Group, and Andrey Seledkin, Product Manager, Digital Technologies.

Maxim Kurtin began his presentation on Astra Linux protection mechanisms, how it protects against information security threats independently and in conjunction with other external information security tools. He started with the regulators: the FSTEC of Russia, the FSB of Russia, the Ministry of Defense of Russia, and Roskomnadzor. The latter's main focus is on personal data. There is also the Bank of Russia, which operates in the financial sector, and the Ministry of Digital Development.

The main current focus in terms of regulatory requirements is the transition to domestic security tools, both hardware and software.

The main emphasis, of course, is on critical information infrastructure (CII) systems. Astra Group has been actively working in this area for many years, starting with the release of the operating system and other products that are part of its ecosystem.
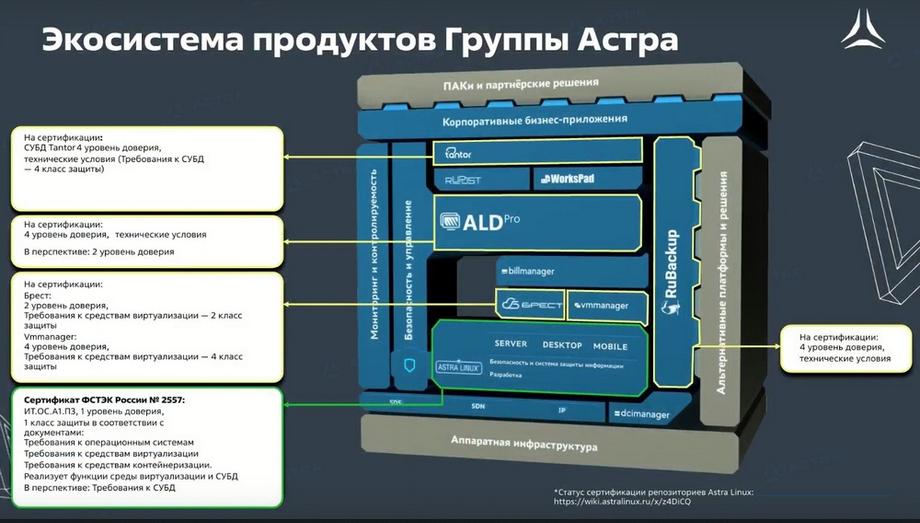
Astra Group now actively seeks to provide its customers with both system and application software that not only functions on its own and helps solve certain tasks but also integrates with other systems, both functionally and in terms of security mechanisms. We are currently actively certifying our products. The Astra Linux operating system is certified by the FSTEC of Russia, the FSB of Russia, and the Ministry of Defense of Russia, up to level 1. This means that Astra Linux can be used at all levels of protection and in any information and automated systems. We are actively pursuing the certification of products such as ALD Pro, Tantor DBMS, RuBackUp backup and recovery system, and the Brest and VMmanager virtualization systems.
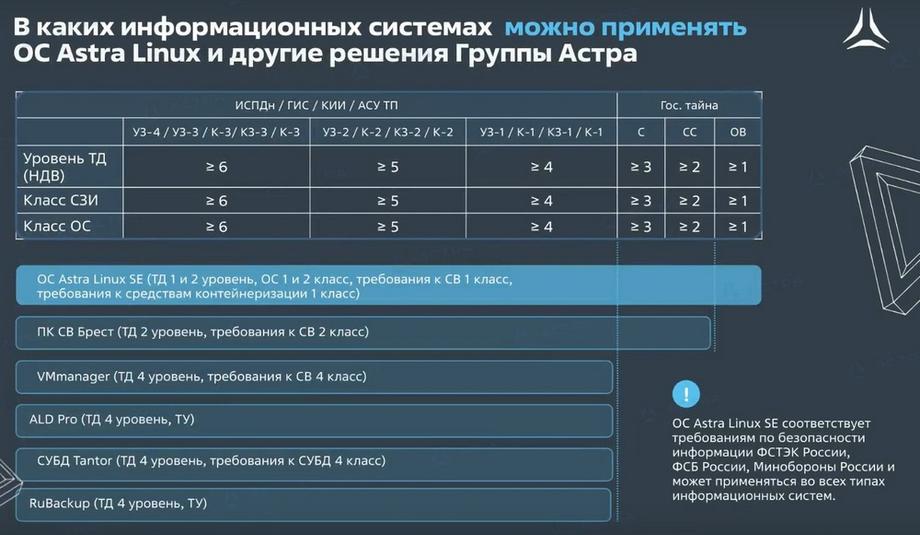
For the most part, these are certifications to the fourth level of trust and the use of these products in confidential information processing systems. But these are just the first steps. Next is Brest, where we are aiming for the second level.
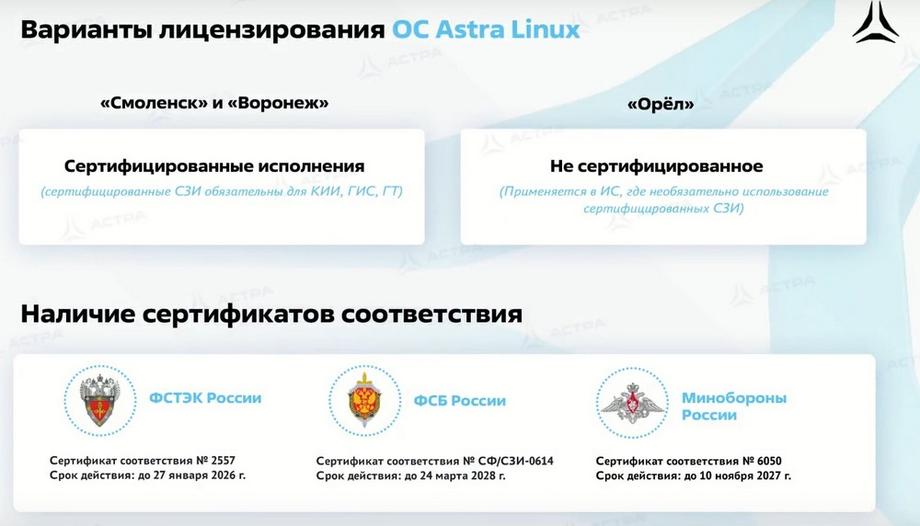
Astra Linux is used up to state secrets, up to OV, and our other products are up to the first classes and levels of protection for confidential systems. The Astra Linux operating system has several versions. The uncertified version is the Orel version. It can only be used where there is no need to protect information, in those information systems where regulators do not impose any requirements. The Smolensk and Voronezh versions are certified for different classes. Voronezh is the operating system version for confidential information processing systems. Smolensk is the classic old version of the operating system, which is suitable for use, including for state secrets. How do they differ?
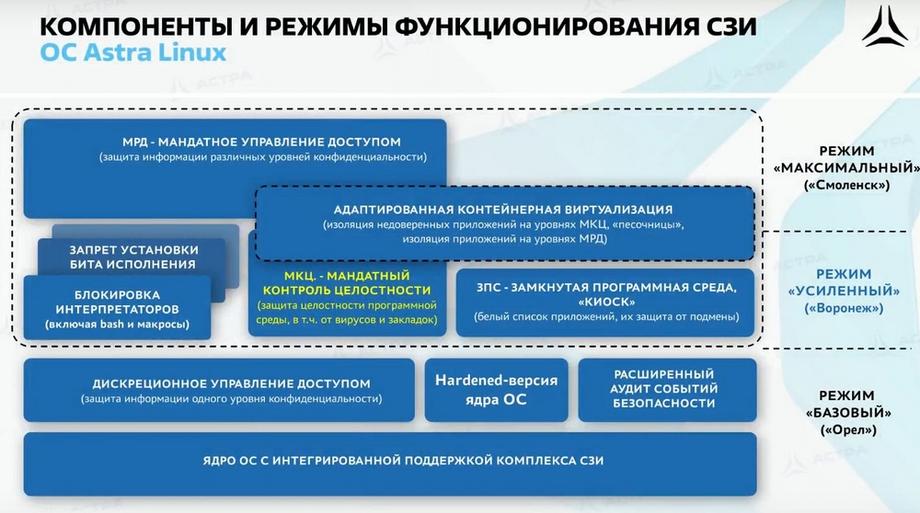
The Orel version is the so-called basic mode. It includes a classic set of protection mechanisms, such as discretionary access control and extended audit. Moving up the level, to the enhanced mode in Voronezh, it already includes mechanisms such as Mandatory Integrity Control (MIC) and Closed Software Environment, KIOSK. In the maximum mode, Smolensk, Mandatory Access Control (MAC) is added. Protection mechanisms include functions such as a closed software environment.
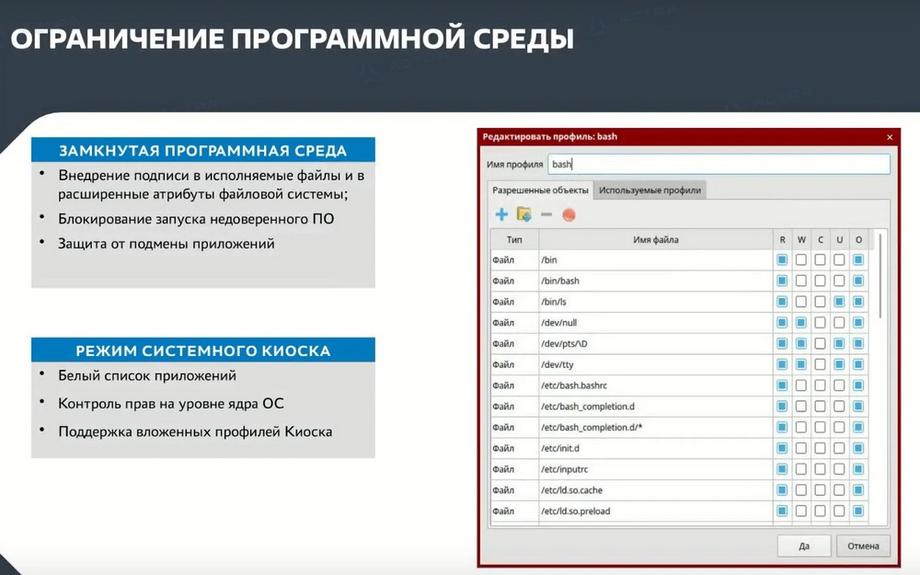
This corresponds to the signing of all executable and launched files with an electronic digital signature issued by our company, all executable files that are part of Astra Linux, as well as all proprietary software released by our partners or other software manufacturers. If the software environment mechanism is running, no file will run without an EDS check. Kiosk mode is a classic application whitelist mode. We only run what is allowed to a specific user, a specific group, and so on.
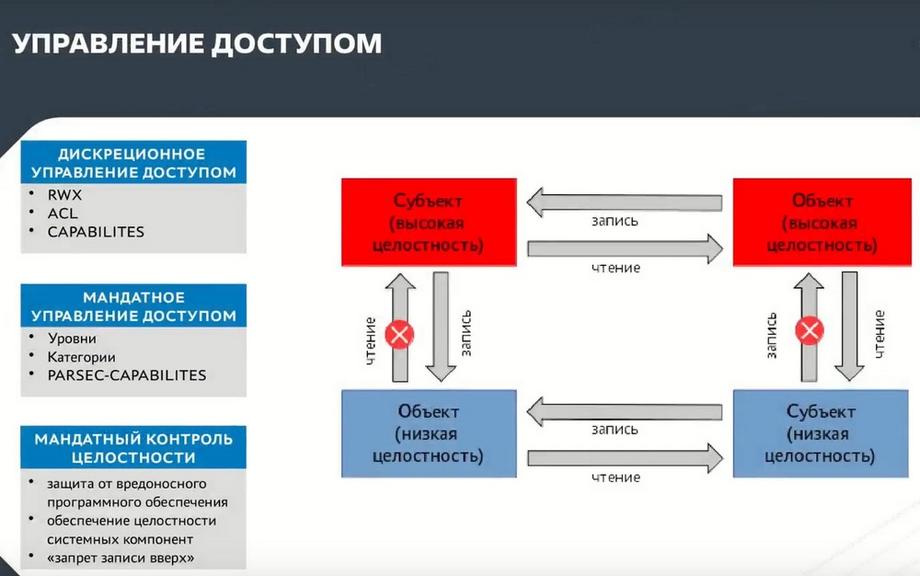
Access control mechanism. It is already more in-depth, it works on access control for reading and writing. Standard classic discretionary access control is standard RVX - read, write, execute by access lists, that is, by file assignment. This is what exists in all operating systems, applications, and so on.
Mandatory access control. This is already a more classic scheme, where we have levels of confidentiality: DSPE, secret, and so on. This is when we can read from above what is below, but not write there. From below, we can write, but not read what is above. But at the same time, our MAC mechanism is supplemented with categories. That is, we not only divide information vertically, but also horizontally. Simply put, we divide information from the personnel department, information from the accounting department, and so on. That is, users, if their categories are equal, have access to this category of information.
Mandatory integrity control. This is a mechanism for dividing all entities within the operating system into levels. Roughly speaking, users work at the zero level, and the administrator is at the highest, the 63rd level. This gives write control. The picture now shows mandatory integrity control. Subjects with the same level can work with each other, and subjects with a lower level will not be able to reach a higher level. This is precisely the control of protection against malicious software, this is ensuring the integrity of system components. That is, we have divided the entire system into conditional 63 levels and control the interaction within the system between each other.
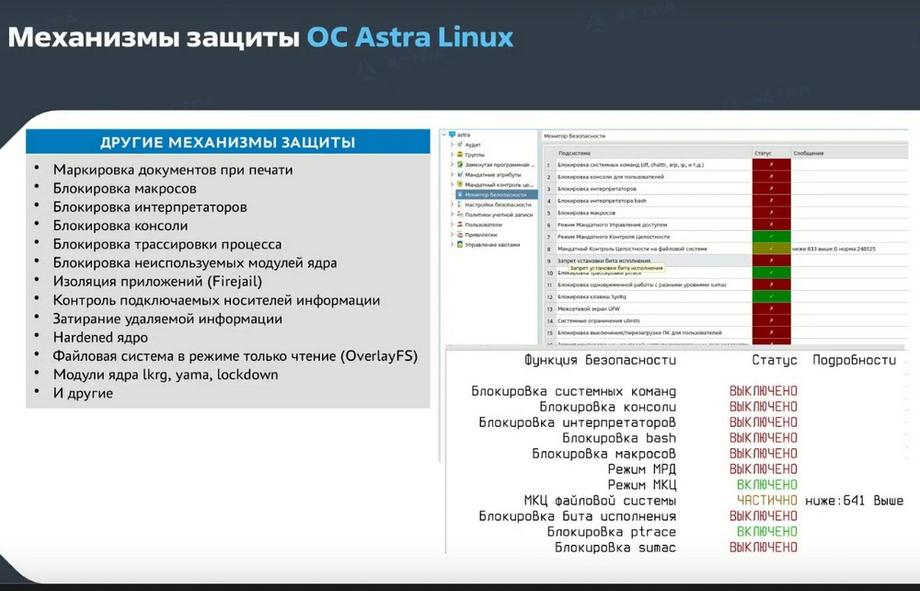
But these are not all the protection mechanisms that are present in Astra Linux. We also have built-in mechanisms, such as document marking when printing, macro marking, interpreter marking, console marking. They have graphical interfaces, they can be turned on and off. Everything is again determined by the security administrator and depends on the degree of threats to the information system, on the requirements imposed on this information system.
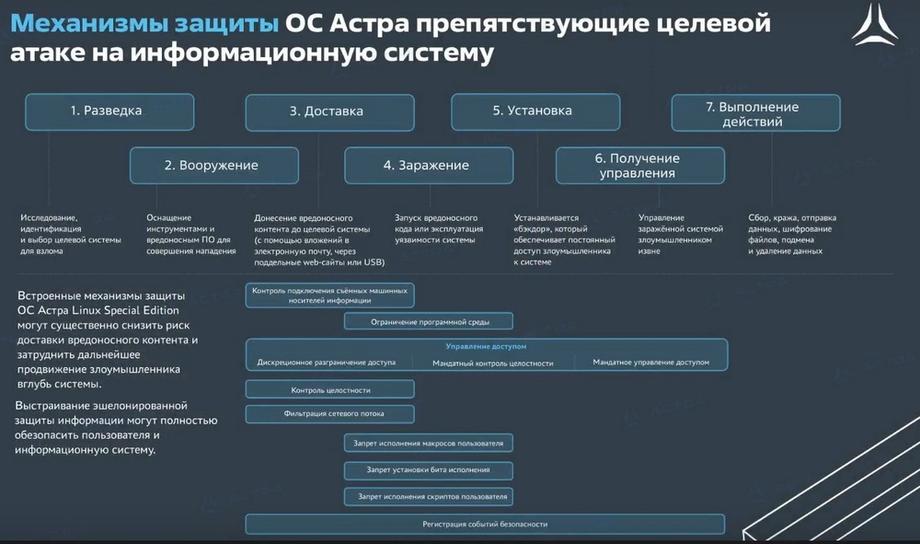
If we consider the entire set of Astra Linux protection mechanisms at a certain stage of an attack on the system, we can say that Astra Linux allows you to stop the attack, stop it, starting from the moment the attacker gains access to the information system, to the operating system itself. And at each subsequent stage, the protection mechanism prevents the attacker from attempting to install malicious software or gaining access. But, unfortunately, Astra Linux OS itself cannot protect against all the threats that exist, fulfill all the requirements that regulators impose on information systems.
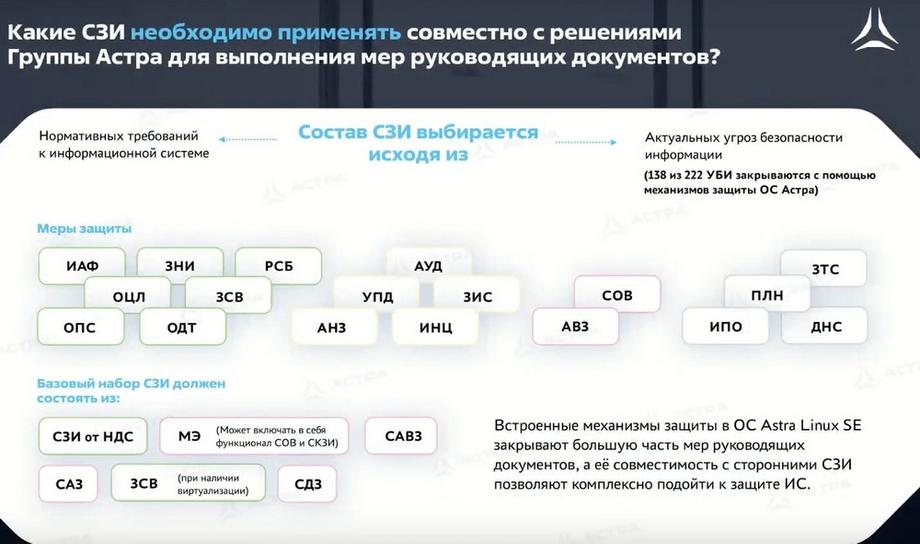
Naturally, we need to integrate and work together with external security tools that will provide a comprehensive security system.
We do not have an antivirus in the OS and it is necessary to protect against the introduction of malicious software, this is a firewall for traffic control, for filtering traffic, a trusted boot tool to ensure trusted boot of the operating system from the desired media and control the integrity of files on the hard drive and the operating system itself at the boot stage. To implement all this, we work with our partners in terms of testing, integrating mechanisms, and some joint development solutions.
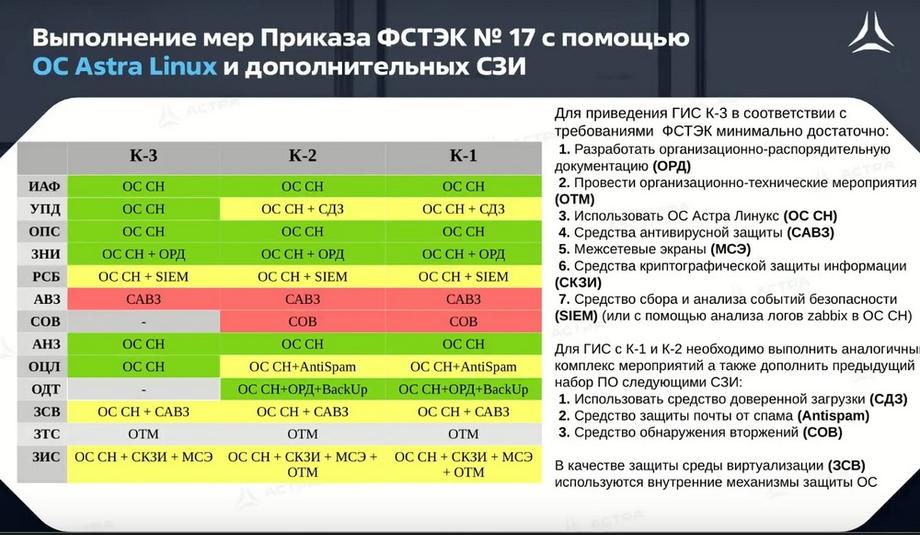
If we consider a comprehensive security system and how Astra Linux itself can help protect, using the example of the same FSTEC Russia Order No. 17, we see that Astra Linux cannot independently provide all security measures. In certain groups of security measures, we need additional security tools, such as Access Control (UPD). There are some levels that are not at all within our control. This is antivirus protection and intrusion detection tools. But by ensuring compatibility with the products of vendors producing external security tools, we will allow you to protect your system from all possible threats.
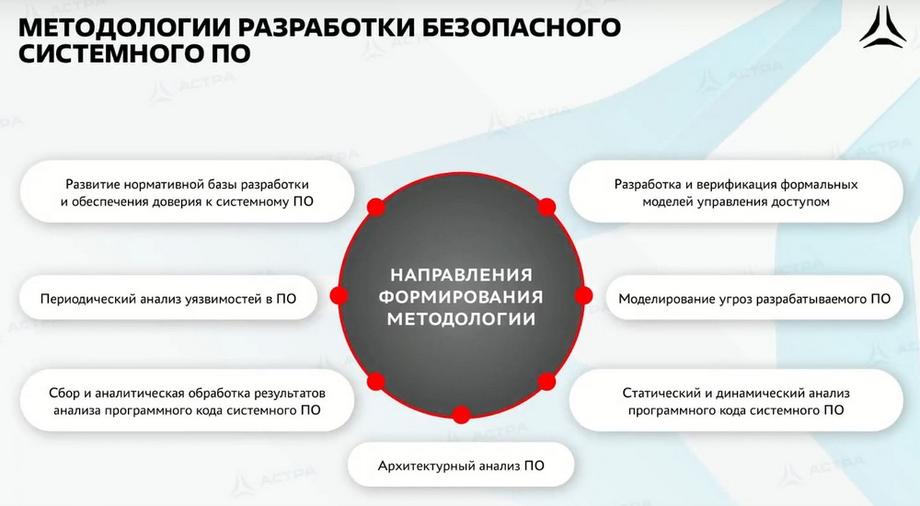
But the security mechanisms themselves, integration with other security tools, will also not be able to ensure maximum security. Therefore, we have implemented a methodology for developing secure system software in the company during product development. It allows us to conduct control of both the source code and the functions of the operating system at all stages of development. Testing is also carried out, including control of delivery, control of the presence of vulnerability searches, and subsequent updates of the operating system. The introduction of security mechanisms, support for external security tools, and a secure software development system - all this together ensures the maximum level of security of the operating system itself. This is GOST 56939, it is open, but it is currently being finalized. But the GOST that is posted is valid and you can work with it.

We also have a service part. We use a product-service strategy, we provide services such as Ready for Astra - this is a service that tests the compatibility of security tools, software, and equipment. We have been working in this direction for a long time and actively. We provide technical support to partners, assistance with implementation, we also provide assistance in developing architecture, security systems, and integration.
Our advantages are shown on the next slide.

We have launched a Bug Bounty program jointly with the company Bizon, where we have provided an opportunity for everyone to check our operating system for vulnerabilities, for the presence of some holes, for the operation of all security mechanisms. Anyone can come in, can participate, can try to hack the operating system. Well, and indeed, if it is a proven hack, then there will be financial rewards.
Then the floor was taken by Andrey Seledkin, Product Manager, Digital Technologies.

We are developers of solutions in the field of secure electronic document management, we have been working in the market since 1999. Our main product is CryptoARM.

We also have a solution for protecting channels for web servers, Thrusted JS. There is Thrusted Java - this is a set of cryptographic algorithms implemented in accordance with the requirements of the JSSE and JCE architectures. For CryptoARM, we have already sold more than a million licenses.
CryptoARM is a program that allows you to sign any document, sign, encrypt, and transmit it to the end recipient at any workplace. This is the direction of submitting electronic reports for interaction with government agencies. First of all, this is the Bank of Russia and Rosalkogolregulirovanie, as well as Rosobrnadzor.

The reporting file is generated at the sender's workplace. Usually, these report files are certified with a qualified electronic signature and encrypted with a certificate of the department in order to safely transmit, for example, through a personal account. CryptoARM is also used for interaction with government portals in terms of obtaining certain government services. For example, in Rosreestr you can get a number of services from registering ownership of real estate, registering for cadastral registration, or challenging the cadastral value of real estate. CryptoARM in this case is used so that you can sign additional documents to applications and requests. These are various types of certificates, document scans. Another option for interacting with the state where CryptoARM is used is electronic legal proceedings, that is, the ability to file lawsuits through the GAS "Justice". CryptoARM is also used to attach materials to applications of various kinds of documents. All of them are certified with a qualified electronic signature. The organization of electronic document management is also ensured, both internal and external. External document management is direct document management between companies, or the exchange of documents with employees, remote employees, remote remote employees, freelancers, or self-employed.
Secure document exchange. Here, of course, an electronic signature is not used, but encryption is used. CryptoARM can be used as a tool to verify an electronic signature.
You can use it as a personal tool to locally verify an electronic signature on your device. At the same time, CryptoARM does not require licenses to verify an electronic signature. CryptoARM is not a completely independent program, it is still some web interface for interacting with external providers. Providers can be both software and hardware. For calls to crypto operations, an appeal is made precisely to crypto providers.

CryptoARM version three differs from the previous version of our product in that it has an built-in mail client that sends documents to the recipient in a secure form. This uses end-to-end encryption technology, while all content and attached documents are encrypted on the device with the recipient's public key and then on the receiving device, it can decrypt both the contents of the letter and gain access to the documents.
There is the possibility of confidential sending of documents and the possibility of sending documents with knowledge of legal significance.
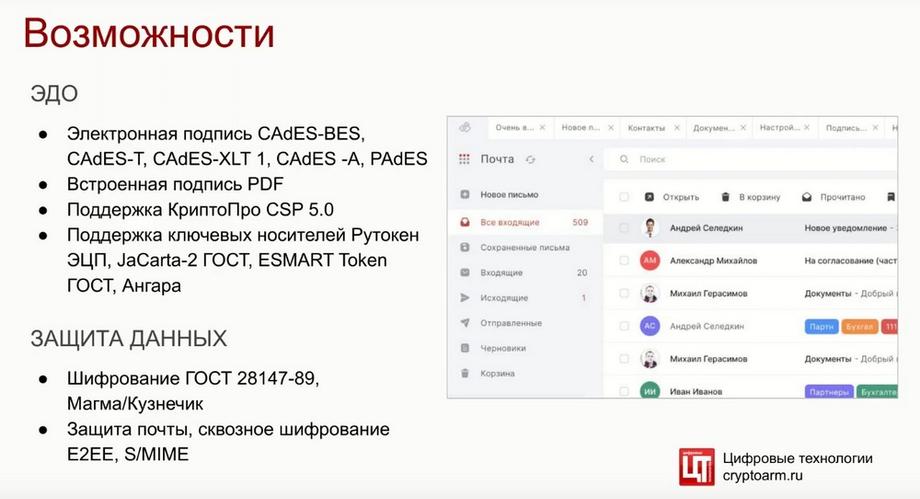
We support different types of electronic signature standards. There is a traditional CMS signature. There is an advanced electronic signature. Signatures with time stamps are supported, signatures with additional attributes. There are signatures that allow you to verify the validity of an electronic signature after the expiration of the certificate itself. An archival signature that allows you to organize long-term document storage for a period of 30 years or more, provided they are re-signed. Also, in the latest versions, we have supported an advanced signature for pdf documents. We also support CryptoPro CSP 5.0.
Now on home

Герой России Гарнаев: никто из профессионалов о возобновлении производства на КАЗ всерьёз не говорит

Система отслеживает спутники на высотах до 50 000 км и ведёт за ними наблюдение

The armored vehicle is equipped with a KamAZ-740.35-400 diesel engine with a power of 400 hp.

Constant improvements in avionics, weapons and tactical capabilities will make the aircraft a flexible response to future challenges

The exterior of the KamAZ-54901 features fairings on the cab and chassis for fuel economy

Fighters are in demand both domestically and abroad

Tyazhpromexport and Venezuela Agree on Plant Revival

The company not only completed the state order, but also quickly mastered the production of AK-12K for special forces

Experts have developed a photogrammetric complex with a resolution of less than 1 cm


