Joint event of OCS distribution company and IVK, a Russian developer of application and infrastructure software, software and hardware complexes, and information security tools. Vendor products: • IVK Kolchuga-K - FSTEC certified software and hardware firewall; • IVK Crypto - FSB certified tool for building cryptographically protected VPNs.
Maxim Orlov, Head of Project Development Department, IVK company, started today's event. Today's meeting will include 4 blocks. I will talk about IVK company, what we do, what our competencies are. In the second block, I will present our new partnership program. In the third block, my colleague Igor Korchagin, Head of the Information Security Department, will talk in more detail about our developments in the field of information security tools.

IVK Group of Companies (Information Implementation Company) is a leading Russian developer of information security tools for infrastructure software products, software and hardware solutions, computer equipment, embedded systems, including those based on domestic operating systems and domestic processors.

IVK has been operating on the Russian market since 1993. As a vendor, based on its own independent set of technologies, it develops a portfolio of certified products and certified solutions focused on government and commercial organizations. IVK has the necessary licenses and certificates, including for work related to the creation of information security tools, for work related to the use of information constituting state secrets.

The company's production facilities are certified according to GOST 1090-1 and allow to produce up to 300,000 units of computer equipment per year. To achieve a high level of reliability, 100% of the products are subject to quality control.

The IVK group of companies includes directly the "Information Implementation Company", the company "Basalt SPO" - the developer of the "Alt" OS family, based on the Russian independent package repository "Sisyphus" and the production complex "Vega". This is our industrial complex for the production of equipment. It is located in the city of Elektrostal, Moscow region.

The end customers are government agencies, commercial organizations, the armed forces of the Russian Federation, and subjects of critical information infrastructure. JSC IVK is included in the consolidated register of organizations of the military-industrial complex of the Russian Federation.

In the activities of IVK, three major areas can be distinguished. These are the development and production of domestic system software based on solutions of international open source projects and based on its own "Sisyphus" repository. The second area is the development and production of information security tools in the form of software and hardware complexes. And the design, development and production of computer equipment, including those based on domestic processors, computer equipment for general and industrial use, servers, monoblocks, computing modules, laptops. Computer equipment is manufactured at its own modern assembly production, equipped with a conveyor line and a thermal chamber for testing.

In the field of software development, the flagship product is the "Alt" family of operating systems. "Alt" OS for servers and workstations, including the secure "Alt 8 SP" OS, which has certificates from the FSTEC of Russia, the FSB of Russia and the Ministry of Defense. The development was based on the principle of ensuring independence from foreign repositories, OS developers based on the Linux kernel. The "Sisyphus" repository is not a derivative of repositories such as Debian, Red Hat, Suse, etc. This ensures independence from the development vectors of foreign repositories and active support at the repository level for processors of Russian architectures, as well as the possibility of developing and producing a domestic OS in conditions of risk of sanctions pressure.

In addition to the "Alt" OS, the company has developed other software products. IVK solutions are used as the basis for building a system of confidential electronic document management in the structures of the Ministry of Defense of Russia and also for the system of automatic processing of citizens' appeals. For these purposes, IVK BUREAUCRAT and IVK POSTFACTOR software products have been developed. All software products developed by IVK are included in the unified register of the Ministry of Communications of Russia.

The second area of the company's activity is the development of information security tools. This is the software and hardware complex firewall "IVK Kolchuga-K" and the software and hardware complex "IVK Crypto".

"IVK Kolchuga-K" is a firewall and communication center for perimeter protection. The first firewall was produced by IVK in 2005. Currently, the fourth generation of firewalls is being produced. It has a certificate from the FSTEC of Russia. The software of the "IVK Kolchuga-K" firewall is developed on the basis of the domestic "Sisyphus" repository and is included in the Unified Register of Russian programs under number 413. IVK firewalls are supplied in the form of software and hardware complexes. The line of firewalls consists of four devices: Kolchuga-K-01, -02, -03 and -04. Three of these devices are produced in the form of single-unit devices for placement in a server rack, Kolchuga K-02 is produced in the Box-PC format. The assembly of the Kolchuga-K software and hardware complex is carried out at the production site of JSC IVK in Elektrostal.

The crypto protection tool PAK "IVK Crypto" is a PAK for organizing crypto-protected virtual private networks. It provides automatic encryption/decryption of information not containing information constituting state secrets. It is assembled on the basis of the Kolchuga-K firewall on the same hardware platform. The line consists of 5 devices. Four single-unit devices for rack mounting and "IVK Crypto X2 P4" is a Box-PC format device, also another Box-PC format device is ARMA-administrator.
The largest implementation, more than 3000 devices, which covers all regions of the Russian Federation, within the framework of the project to ensure the protection of information transmitted within the framework of a single information space of courts of general jurisdiction and subsequently magistrates' courts and the "Glas of Justice" system.

And the third area of the company's activity is the production of computer equipment. VT development of IVK company for general and industrial use, servers, personal computers, monoblocks, laptops.

The equipment is designed for operation, including in harsh conditions, including dust, moisture, high and low temperatures, vibration and shock. The company's production activities are based on domestic technological achievements. In particular, all elements of the mechanical part of the structures and to a large extent electronic and software components are based on the company's own developments.
The Information Implementation Company has launched its own partnership program, which defines a new procedure for IVK's interaction with partners in promoting IVK's software and hardware complexes. In this case, we are talking about the supply of information security tools for the Kolchuga-K firewall software and hardware complex and the IVK Crypto software and hardware complex.

As part of the IVK partnership program, different types of partnerships are provided depending on the competencies. Partners are assigned different statuses: distributor - a legal entity that has competencies in the supply of vendor products and distributes its products through its partner network; authorized partner - a legal entity that does not have direct contracts with the vendor, but has the opportunity to work with the vendor through a distributor under the terms of this partnership program. Authorized partners include the status of dealer and technology partner. There is also another status, which is a strategic partner. These are legal entities whose turnover with IVK exceeds 50 million rubles and who have experience in integrating into the end customer's infrastructure, including in complex solutions, and providing technical support services.
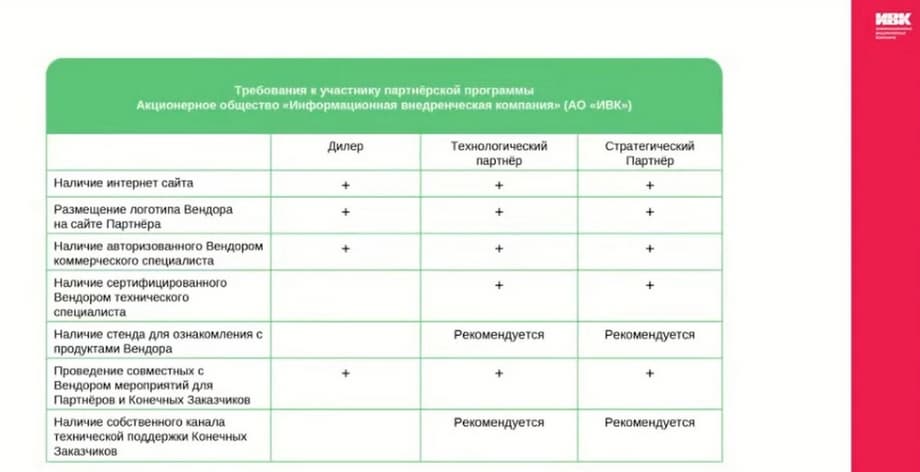
Strategic partners purchase products directly from the vendor, authorized partners, dealers and technology partners work through a distributor under the terms of the partnership program. Shipment of IVK products is allowed only to partners who have joined the partnership program. The partner status is determined by the vendor in accordance with the requirements shown on the slide. We provide the partnership program with applications upon request by email or through a distributor. Joining the IVK partnership program is carried out by signing a consent to participate in the partnership program.
The main difference between a partner with the status of a dealer and a partner with the status of a technology partner is the presence of a technical specialist certified by the vendor. Which also allows the technology partner to provide technical support jointly with the vendor.

IVK has developed and provides training for partners to deepen their knowledge of the company's products. Following the training, certificates are issued from the vendor and from the training center. 2 courses have been developed: the "Kolchuga-K" firewall administration course, with a duration of 3 days, and the "IVK Crypto" software and hardware complex administration course, with a duration of 5 days. The authorized training center is the St. Petersburg Polytechnic University named after Peter the Great. Training takes place in our office in the training class at the address: Moscow, Butyrskaya str., 75. It is possible to take the course both in person and remotely.
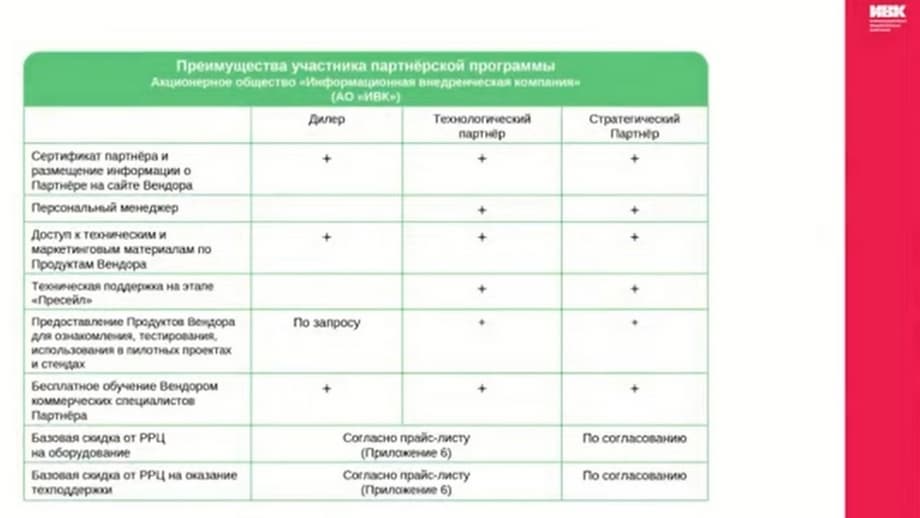
A company that joins the partnership program gets access to all the necessary information about the program and IVK products, technical and marketing support from the vendor, as well as the opportunity to train and certify its specialists. Technology and strategic partners also receive a dedicated personal manager and technical support.
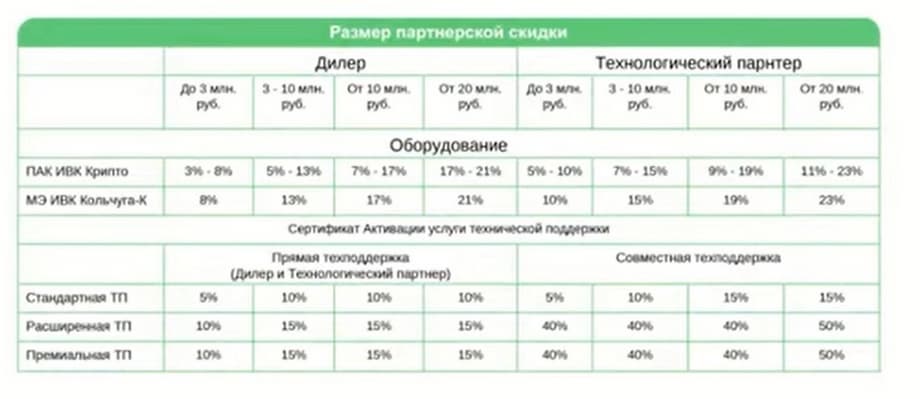
The size of the partner discount depends on the partner's status, the technology partner has a larger discount than the dealer, and on the volume of sales of the vendor's products. I would also like to draw your attention once again to the fact that the technology partner has the opportunity to provide joint technical support with the vendor. Joint technical support is provided as part of extended and premium technical support. And discounts on technical support certificates are higher in the case of joint technical support. The partnership program also outlines the procedures for protecting the transaction and more detailed mechanisms for interaction with the end customer, distributor, vendor and partner.
Then the floor was taken by Igor Korchagin, head of the Information Security Department of IVK.

He focused in more detail on the specific technical solutions of our products related to network protection. This is the IVK Kolchuga-K ME software and hardware firewall. He said that in some moments I will repeat myself on the composition of our solutions, but with a deeper immersion in the technical specifics.
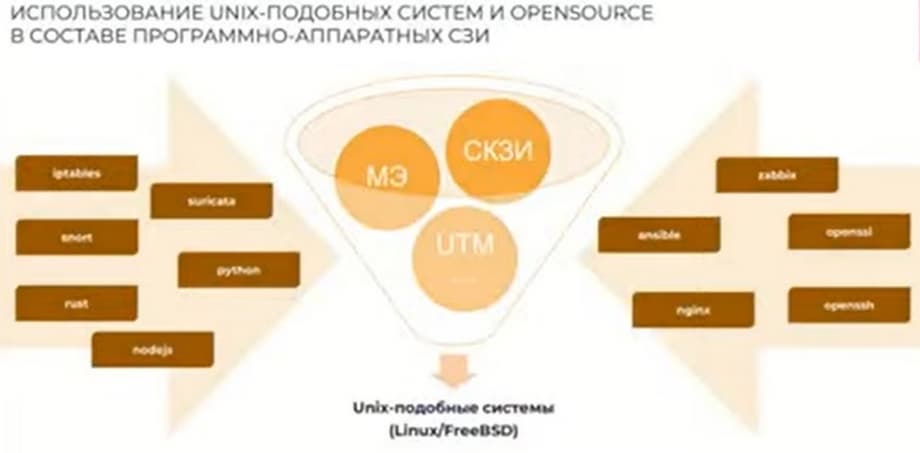
How we came to our solution. Our company in the field of software development in the IT market has been around for more than 20 years. How we came to the task of developing our own firewalls. When we started researching the market of existing solutions more than 15 years ago, we understood how existing firewalls are formed, including foreign ones. Communication equipment is mainly the use of various OPENSOURCE, i.e. proprietary development that functions on unit-like OS such as Linux, FreeBSD and others. After studying this market, we came to the conclusion on how we can start this work.
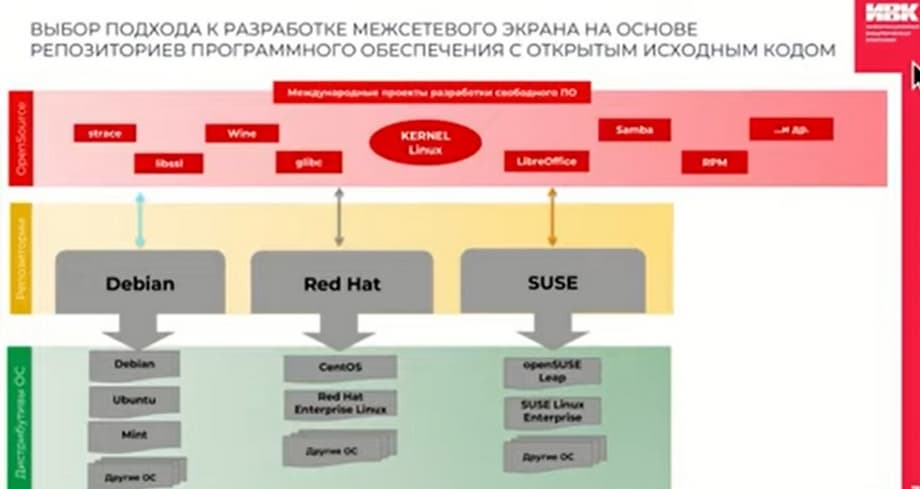
And we realized that at the heart lies a huge amount of OPENSOURCE and OPENSOURCE repositories. We realized that no one solves this problem by working directly with OPENSOURCE, everyone is guided by some distribution that is supported by the largest open communities. The slide shows Linux-like repositories, the vendor, planning its development, chooses some repository, and further development of its software hardware complex and software solution is carried out taking into account this repository. At the same time, working with OPENSOURCE directly is impossible due to the huge number of dependencies. There is a scheme, we choose the basis of the repository with which we work, consisting of OPENSOURCE, and formulate our solution. And this approach is used by most developers of IT equipment and storage facilities. After studying this market, we realized that there are many options, but they are all foreign. And we tried to figure out if there is anyone in our market who represents these ideas, while being a resident of the Russian Federation and has sufficient competence? Then we met a company that had its own domestic repository. It was called "Sisyphus", and it was completely equivalent in terms of principles and approaches that are supported by foreign repositories, but at the same time it is accompanied exclusively by our specialists, domestic developers, who are also active participants in the international community. Their contribution at the level of OPENSOURCE repositories, and also gets into foreign repositories. The slide shows the composition and volume of data packages of these repositories for a huge number of architectures. At that time, 16 years ago, the issue of architectures was not as relevant as it is now.
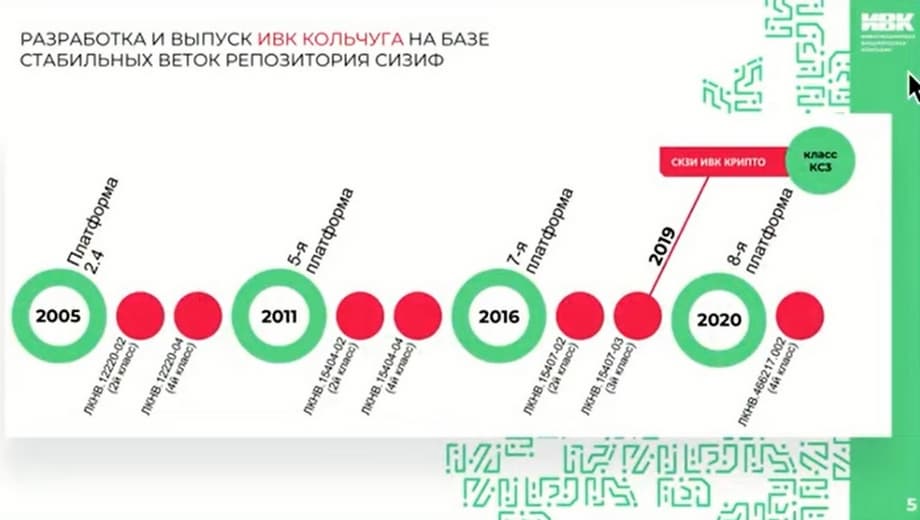
Then everyone considered exclusively the x-86 architecture. But, having laid the foundation for the approach of the domestic repository then, we got a flexible opportunity to switch to other hardware architectures. And so the "Kolchuga-K" firewall was born. The slide shows the history of his life. Its first certified version was released in 2005 on the 2.4 Linux platform. 2 products were released according to the RD requirements for firewalls. In 2011, we released the second generation of the product. It was already the fifth platform from Linux at its core. In 2016, the third generation was released on the 7th platform. Starting with the third generation, we have the IVK CRYPTO SKZI product, which is built into our PAK. There was certification according to the KS3 class. And since 2019, these two products together. And in 2020, the fourth generation was released, which is the basis for both our firewall PAK and our information protection PAK. They are certified according to the fourth class. We abandoned certification for state secrets at that time due to some commercial reasons.

And they began to develop the fourth generation line. Four versions of the PAK have been released based on this fourth generation. What are the basic functional capabilities? These are management functions that involve both management through the interface and through the console.
Two roles of administrator and auditor are built in, there are various notification mechanisms for selected categories of security events, group management by lists of IT addresses, various mechanisms for communication management functions, network bridges, static and dynamic routing. Since we have a firewall - this is filtering network traffic at all levels of the IC model, including deep packet analysis, working with mandates and labels, the redirection mode is used, there are built-in proxy functions for htp and ftp and various mechanisms for stability and reliability, multivana support, the ability to reset the device to factory settings and, one of the most popular at the moment for large enterprises - this is the possibility of integration with various ICM.
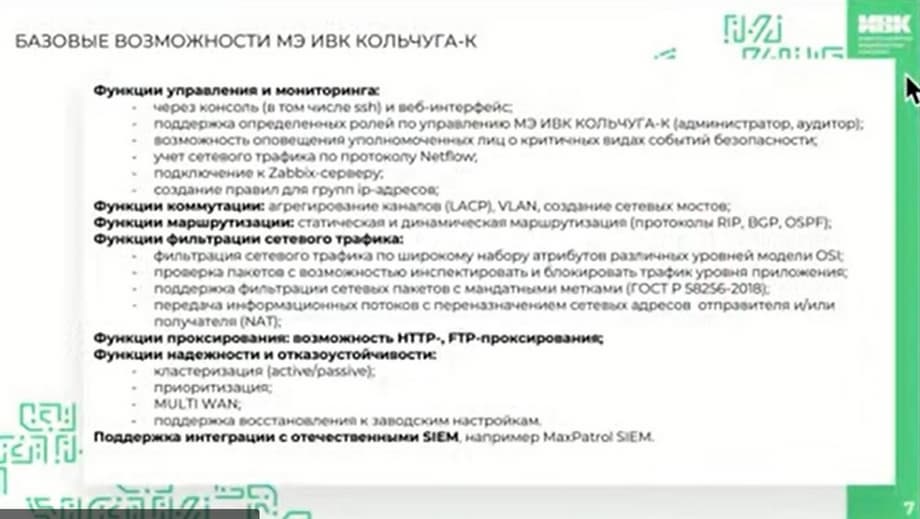
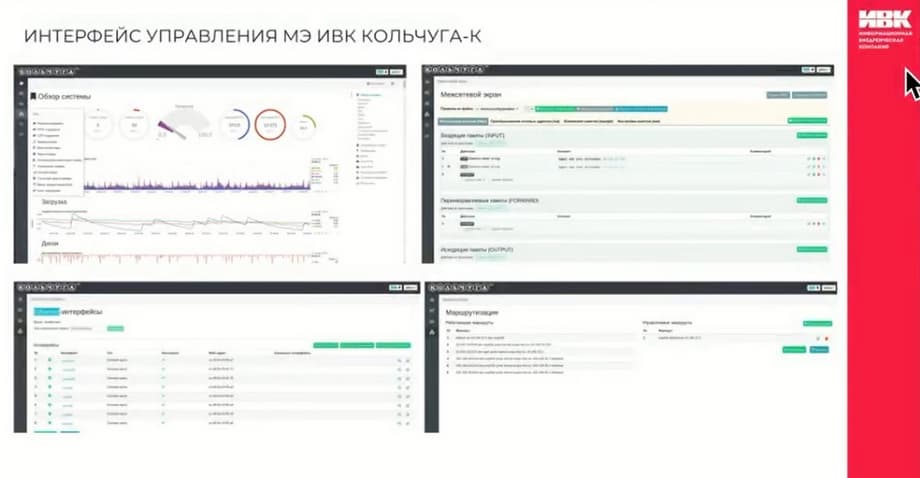
The slide shows an example of the firewall management interface. We are always ready to provide remote access so that you can test, see the capabilities, and experiment with how to work with it yourself.

A few words about the line of IVK Crypto SKZI products. This product is built on the basis of the fourth generation of the IVK Kolchuga firewall. PAK SKZI IVK Crypto is a composite product, at the heart of which you get the Kolchuga firewall itself, as well as additional functionality in the form of cryptographic protection functions. This PAK is called "IVK Crypto", it also has an FSB certificate, and is included in the Register of domestic software. It is available in several versions. Here are crypto gateways in various hardware platforms, control centers and software clients.

Basic functional capabilities are encryption tasks in accordance with domestic GOSTs, various functions of centralized management and monitoring, as well as management through a console interface, the ability to create an unlimited number of managed nodes of virtual networks, event logging. All centrally generated configurations are sent directly to the end devices automatically through the corresponding message brokers, which ensures guaranteed configuration behavior even if the device was unavailable and then turned on, it will receive this configuration.
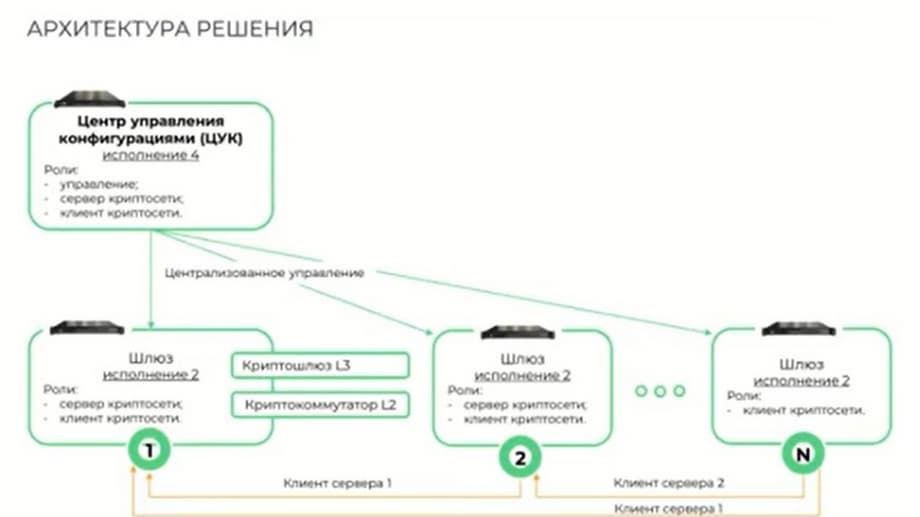
This version can have 4 roles. This is a key task, a management function, and this device can also act as a crypto network server or a crypto network client. The role is determined by the configuration formed by the administrator of the configuration management center.
The next block is the crypto gateway. This is version 2. It can act as both a crypto network server and a crypto network client. Regardless of the mode in which it will be operated, either in crypto gateway mode or in crypto switch mode. I would like to clarify the peculiarity of its role-based construction. The complex itself assumes the possibility of any configuration of complex networks, determined directly by the administrator. And this is not regulated by the licensing policy. By purchasing a gateway of the appropriate version, the administrator can configure the following network through the control center, for example. When we have N number of crypto gateways, where one crypto gateway acts as a client of the server, for example, number 1, and the other acts simultaneously as a client and server 1 and server 2. For example, we have two geographically separated branch facilities in the building. We build one network between them, where we connect them to each other. And there is a central office. Both of these gateways are clients of this central office.
Now on home