Joint event by OCS and NGR Softlab, a Russian developer of intelligent security management systems – SIEM, PAM, and behavioral analysis solutions. The meeting will include an overview of NGR Softlab products with analysis of unique cases.
Event program:
- About NGR Softlab;
- Infrascope – a comprehensive product for privileged access management;
- Structure and capabilities of the Alertix SIEM system;
- Dataplan – an analytical platform for cybersecurity;
- Partner program.
NGR Softlab speakers:
- Andrey Sozin, Head of Partner Relations;
- Alexey Isaev, Head of Technical Sales Support.

NGR Softlab was founded in 2019. Currently, our headquarters are located in Moscow. We are a fully Russian developer.
We have over 70 employees. More than half of them are developers. We have all the necessary licenses and certificates. We are residents of Skolkovo and the Moscow Innovation Cluster.
Currently, we have 3 classes of solutions in our portfolio. The first product is Dataplan. This is an analytical platform for solving information security tasks, and there are currently no analogues on the Russian market. Alertix is a SIEM system. It has an FSTEC certificate for the 4th level of trust. It is worth mentioning that one of the largest commercial SOCs in Russia is built on the basis of Alertix.
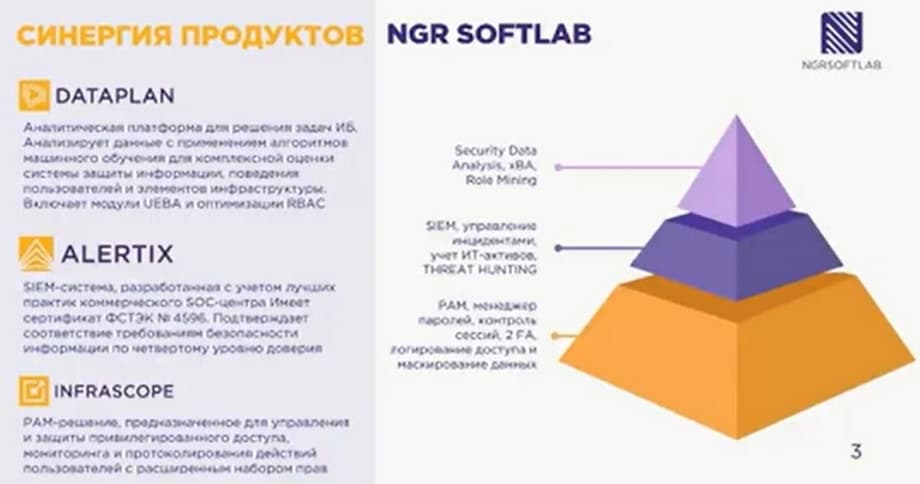
And initially, the entire system was designed as a solution on the basis of which you can deploy a key from scratch. Infrascope is our third product. It belongs to the PAM (Privileged Access Management) solution class. I will hand over to Alexey Isaev, Head of Technical Sales Support.
Let's start with Infrascope. I will try to briefly touch on the technical details of the solution's capabilities. I will mainly talk about the functional capabilities. So, Infrascope is a PAM solution. All of its main functionality works in "Bastion" mode. This is when the solution is a single point of entry for privileged users when they connect to some target systems.
INFRASCOPE
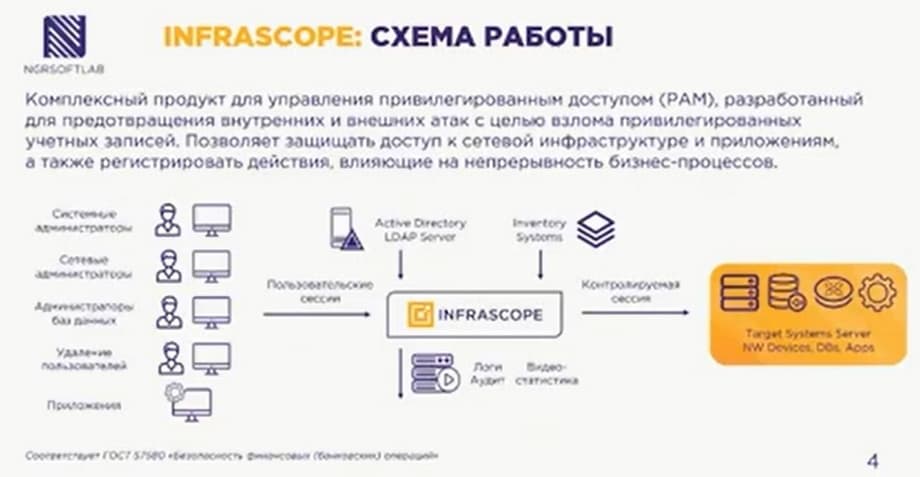
Users can be both employees of organizations connecting to the network or remotely, as well as external contractors, as well as external applications or internal automation scripts. Infrascope is a modular product, it is supplied through sets of modules. By default, all versions of deliveries include password managers, session managers, and two-factor authentication managers. From additional ones, there is also a TOCACS+-manager, data access manager, and AAPM-manager.
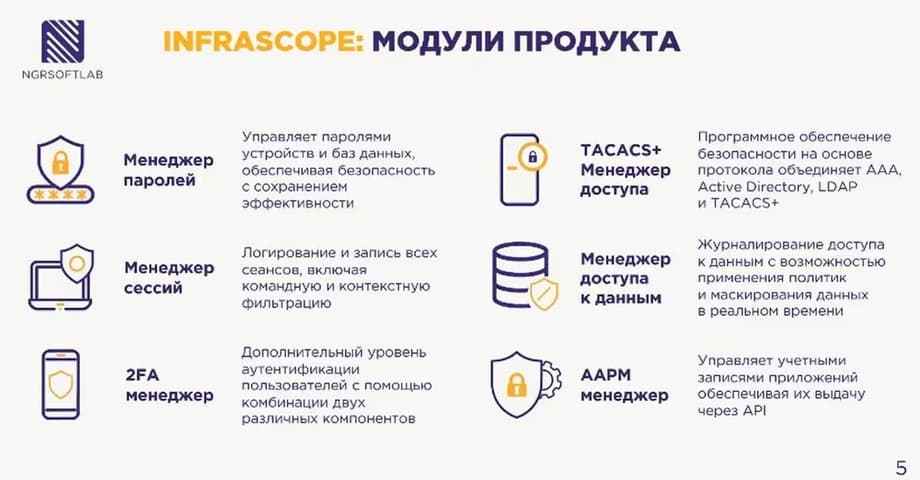
The password access manager is responsible for storing passwords. Passwords can be stored static, dynamic accounts, target system records, domain user records. Regarding the methods of entering passwords, there are uploads from directories, such as entering through a web interface, platforms, entering a password through synchronization of the directory service from Microsoft. The password manager is also responsible for applying the policy. Minimum password requirements. Length, content, symbols, password rotation according to some, for example, schedules. There is also rotation based on some triggers. For example, after each password issuance to a third-party application, you can rotate the password. After each session that was conducted with an internet connection, you can also perform rotations. There is a list of system triggers, and actions can also be linked to them.
The session manager is responsible for logging session records, including command and context filtering. There is a video format where there are timestamps for command execution. You can quickly go, see what the user had on the screen at that moment. Also, for all protocols, there is a text blog. Two-dimensional two-factor authentication. Delivery can be carried out either via mail, or by integrating with a smart gateway, or you can simply upload the "secretkey" mobile application and generate a code in this mobile application. Of interest: two-factor authentication works on the basis of a radio server and can be used for the operation of third-party applications within the organization. And vice versa, if the organization is already using some solution based on two-factor authentication, on the basis of a radio server, then we can already synchronize and integrate with it and use the existing solution to deliver the second two-factor user. That is, it is convenient to integrate as you like.
Only three additional modules are presented here, in fact there are more. The TOCACS+ access manager allows you to replace a full class 3 server and the TOCACS+ protocol. It combines all the advantages of the TOCACS+ server and all the advantages of the solution. This is the use of policies, the use of additional protection mechanisms when a user accesses. And this is full logging of the session record: when it was accessed, who accessed it, what entities and commands authorized it. That is, there is also full logging and relation.
Regarding the additional data access manager. allows you to connect to various databases through Infrascope in Proxy mode using standard protocols, using native ports and native clients. At the same time, Infrascope will apply policies, black and white lists of executing some commands and requests within the framework of access to the database will be available, and full recording control will be carried out. Of interest. You can also mask data in real time, i.e. you can transfer some database to a third-party development or to a third-party department and not be afraid of leaking some sensitive information. That is, the data can be masked, some policies can be applied, for example, replacing characters, mixing up characters, simply cutting off or replacing with some templates.
There is also an AAPM manager - Application to Application Pusset Manager. Through it, you can issue stored secrets and some third-party applications, automation scripts. You can apply various protection mechanisms, such as checking the token, checking the transmitted pin code, checking the control file, so that you can additionally set the number of times this token is triggered and its lifetime. You can make the token one-time and issue the password once, or you can make the token valid for several days, and after several days this token will no longer be active. You can configure which policies will be applied to this application and configure which accounts are available to this application. That is, we either give a password from one account or from several, from a group of accounts, all this can be configured.
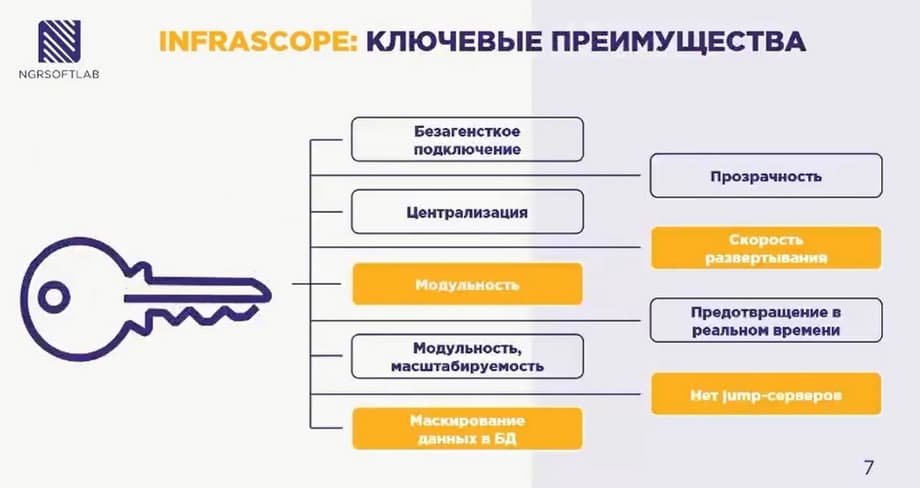
Our main advantages. The solution is agentless connection, i.e. there is no need to install an agent on the end hosts to which we connect, and also no agent is required on the administrator's machine in order to connect to the system. We have various modules, so we can deploy and purchase licenses only for the functionality that is really necessary for the customer to solve his current infrastructure task. Also, our solution is modular and at the same time it is easily scalable. We can choose such a unit as a server and assemble a cluster of three, four, five, ten nods, etc. You can also move separate functionality to separate servers. We can move the functionality of accessing these databases to a separate server and add additional resources to it and use it for accessing databases. We also do not have jump servers, i.e. we do not have servers on Windows architecturally. Therefore, the cost of implementation, the cost of ownership of the solution is reduced, the total number of points of failure in the system is reduced.
And there is also an interesting functionality, this is data masking. There is also an additional function of small privatization of privileged tasks. It helps to solve completely custom tasks for the customer. For example, recently for one very large company, we solved the problem of managing passwords in configuration files. These passwords were stored in plain text, in write-offs, in storage services, and rotated very rarely, about once a year. Through task automation, we first rotated the password for the database to which these services connected, we rotated the password and saved it. Then the task automation went already in the list of end servers. For such a script specifically with Infrascope we got certain advantages precisely because this script can be rotated, for example, once a month, you can track its launch in a full-fledged log of the launch history of scripts, we can see what systems returned as part of this crypt's work.
ALERTIX
ALERTIX is a SIEM system, it was originally developed for commercial use. It turned out to be unique to a certain extent, it has a whole set of modules, all sets of rules of correlation, all sets of functionality, they are on the one hand quite optimal, and on the other hand, we can supply our expertise together with the product.
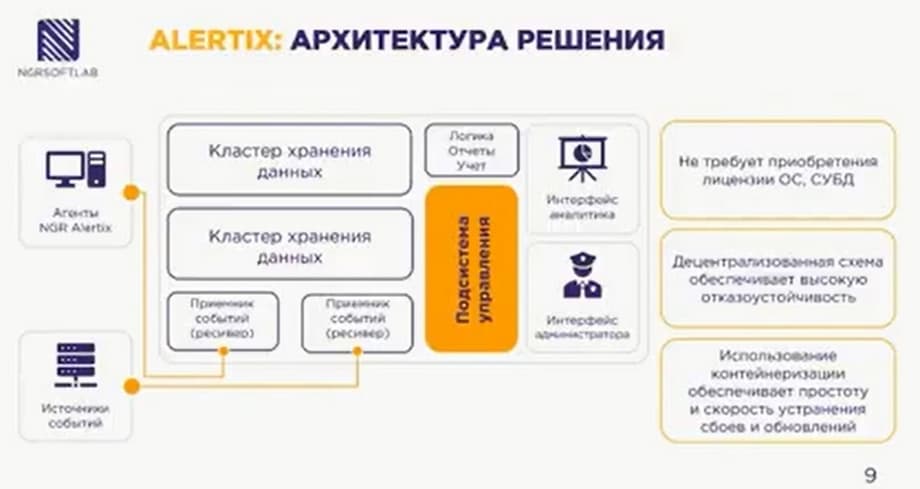
By architecture. The system has three components: the receiver is responsible for receiving events, the storage cluster and the control subsystem. If we talk about interesting points of the architecture, the receiver can process the data coming to it and store in the storage subsystem only what came to it, for example, if some system feeds too much data to the input, and less is needed for the correlator to work, then it is this data that will go to the storage system, the rest will be cut off. The system can correct the time, some incorrect encoding, i.e. additionally help. There can be any number of storage clusters. The control subsystem can update its components separately from each other.
ALERTIX does not require the purchase of DBMS and OS licenses. It is decentralized, therefore it provides high fault tolerance. The use of containerization ensures simplicity, speed of updating and troubleshooting.
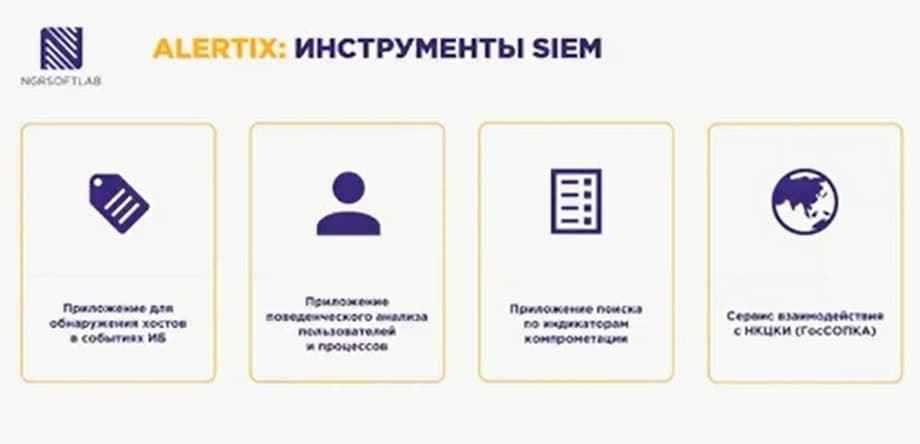
Now about the modules. In general, SIEM implies a Security Information and Management system. Accordingly, in the classic version, this is the collection and correlation of events and accounting for these events. But now SIEM is supplied as a set of products that helps to partially replace or replace existing processes and tools. What comes as additional tools that are supplied together with SIEM?
- Applications for detecting hosts in security events.
- Applications for behavioral analysis of users and processes.
- Applications for searching for indicators of compromise.
- NKCCI interaction service (GosSOPKA).
What is the purpose of inventorying your infrastructure, knowing what subnets there are, what hosts there are, machines, everything that the first application gives? This can help in investigating incidents. If suddenly dozens of new hosts or MACs or IP addresses appeared in the system, then this can help the information security analyst. But the main task of inventory is to prioritize and categorize security events. For example, changing the IP address on the host, if this is a user segment, then this event will not lead to any incident, if the same event is found on some machine or host that belongs to the server segment, then this may already be dangerous.
As for the behavioral analysis application, it comes as a black box, i.e. the rules are written in the administrator's guide and cannot be changed. The application learns the infrastructure for one week, looks at what appointments are normal for this infrastructure, and in the 2nd week it starts to be useful. For example, a bookkeeping PC started scanning the network, on the one hand it is not prohibited, and on the other hand it is strange.
As for the application for searching for indicators of compromise, this is a cache of the sums of suspicious files, these are IP addresses from which attacks were carried out, everything that was once noticed on suspicious viral activity and activity, all this can be packed in the form of indicators of compromise. The delivery of indicators is supplied from the outside. All incoming events are checked for the presence of these indicators, for example, the user went to a prohibited IP address, this becomes suspicious. There is also a lifespan of these indicators.
The NKCCI interaction service (GosSOPKA) is simple. The FSB created the GosSOPKA service throughout the country, there are organizations that must report on this service. There is a need to report on incidents. There are incidents for which there is a deadline by which you need to report.
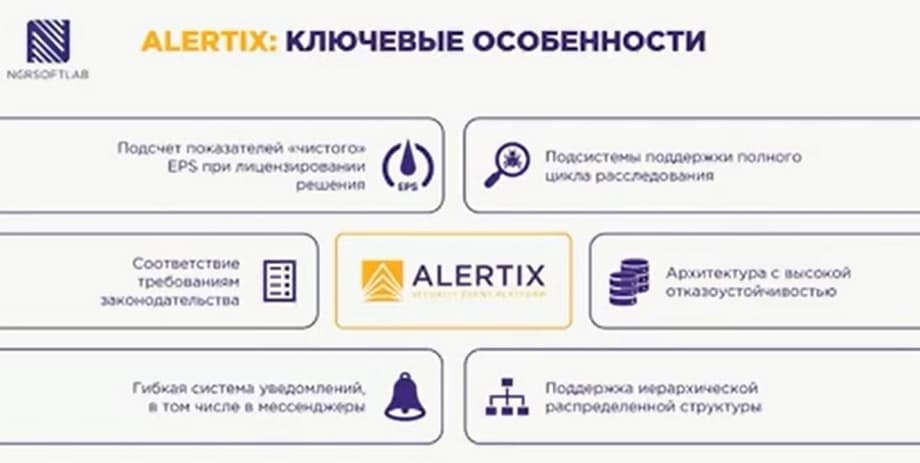
What are the features of ALERTIX? This is the calculation of the "clean" EPS indicators when licensing solutions. We do not include the maximum value per day or the average per hour in the license metric, we take the average EPS value per week. This reflects the load on the correlator, on storage systems. We have a flexible licensing policy, therefore, if your organization is attacked, then you may have exceeded twice the possible number that you purchased. There will be no disabling of functionality, the system will continue to work fully.
DATAPLAN
is an analytical platform that allows you to collect, store and analyze large data sets using machine learning algorithms. This analysis can be carried out by analysts to create custom reports and outputs in the form of tables, diagrams and raw data, in the form of reports.

There are also plug-in modules, among them – xBA. This is an extended behavioral analytics, it solves the following tasks: identifying compromised credentials, detecting insider activity, tracking security policy violations, detecting hidden malicious activity.
The ROLE MINING module, which forms role models. It solves the following tasks: automatic construction of an access control model based on roles, updating information about the state of the access control system, auditing the state of the directory service.
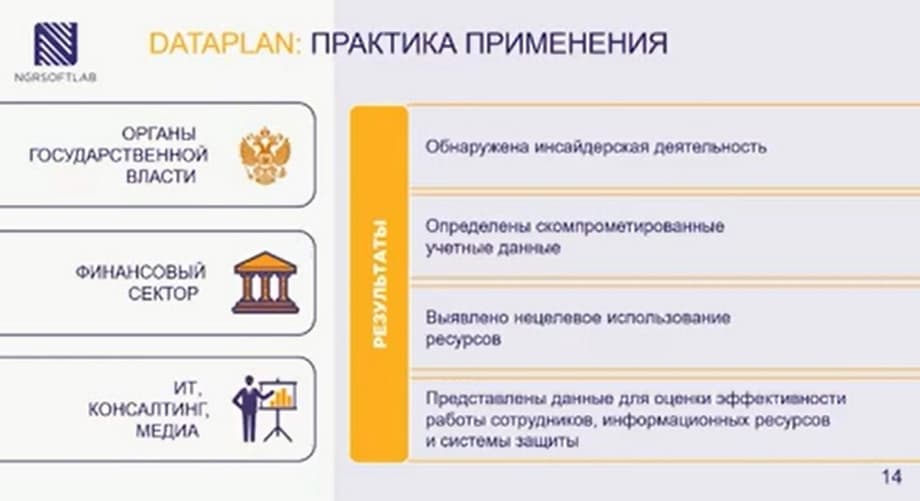
DATAPLAN has already been implemented in several organizations, it helps with insider activity, in identifying compromised credentials, in identifying misuse of resources, in presenting data for assessing the effectiveness of employees, information resources and protection systems.
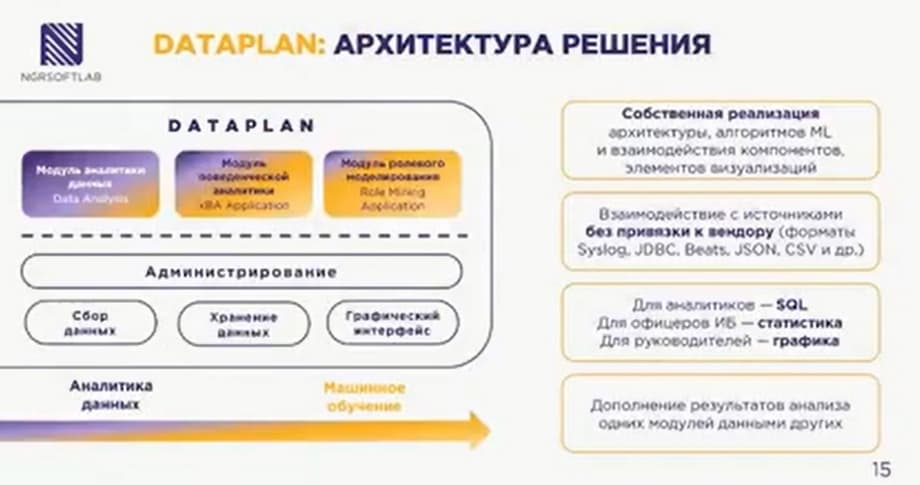
As for the architecture, DATAPLAN also consists of several modules, it, like ALERTIX, has a receiver that receives data, stored data can also be pre-processed and transferred to the storage system only those of them that we need for work. The data analytics module helps to generate reports.
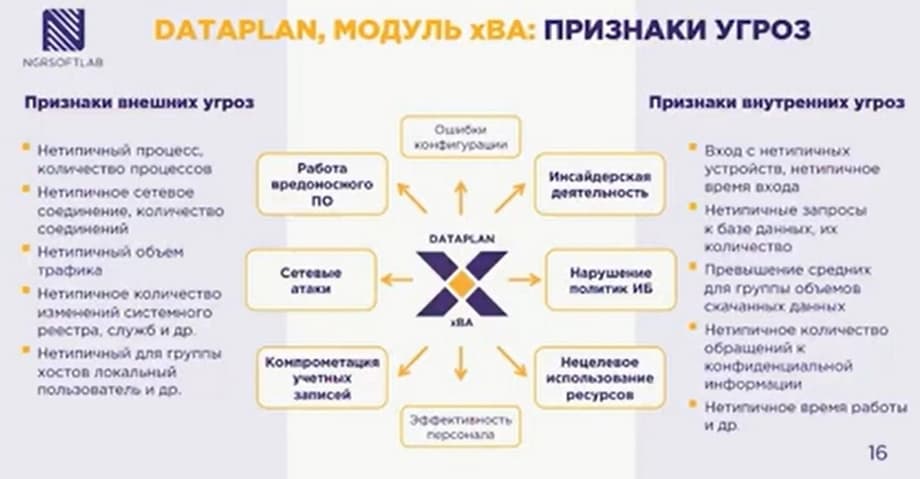
Now about the xBA module for detected threats. You can identify some anomalies and highlight to the information security administrator that these processes are anomalous based on atypical behavior, based on the atypical number of processes.
DATAPLAN, the ROLE MINING module connects AD as a data source, the directory service is divided into entities, roles are formed, it is tracked in which groups a person is, what rights are assigned to these groups, how the account data of this employee is filled in the directory, to which department he belongs, what is his position.
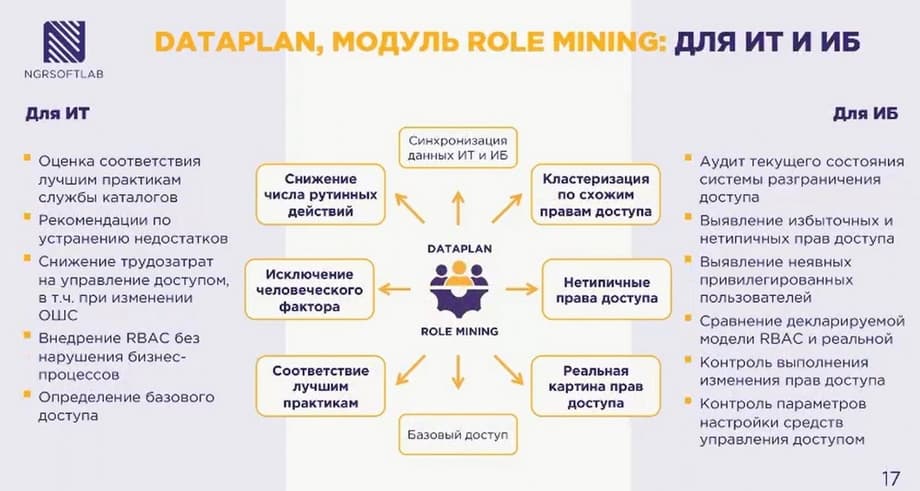
Based on this role model, such parameters as large group nesting are built, very often during directory administration there are some migrations by positions, by departments, some users may have access to where he should not have access according to his current position, we track this situation and issue a more optimal role model.
Now on home

Герой России Гарнаев: никто из профессионалов о возобновлении производства на КАЗ всерьёз не говорит

Система отслеживает спутники на высотах до 50 000 км и ведёт за ними наблюдение

The armored vehicle is equipped with a KamAZ-740.35-400 diesel engine with a power of 400 hp.

Constant improvements in avionics, weapons and tactical capabilities will make the aircraft a flexible response to future challenges

The exterior of the KamAZ-54901 features fairings on the cab and chassis for fuel economy

Fighters are in demand both domestically and abroad

Tyazhpromexport and Venezuela Agree on Plant Revival

The company not only completed the state order, but also quickly mastered the production of AK-12K for special forces

Experts have developed a photogrammetric complex with a resolution of less than 1 cm


